Kody's Latest Posts
 How To:
Control Network Traffic with Evil Limiter to Throttle or Kick Off Devices
How To:
Control Network Traffic with Evil Limiter to Throttle or Kick Off Devices
 How To:
Target Bluetooth Devices with Bettercap
How To:
Target Bluetooth Devices with Bettercap
 How To:
A Hacker's Guide to Programming Microcontrollers
How To:
A Hacker's Guide to Programming Microcontrollers
 How To:
Use Photon Scanner to Scrape Web OSINT Data
How To:
Use Photon Scanner to Scrape Web OSINT Data
 How To:
Mine Twitter for Targeted Information with Twint
How To:
Mine Twitter for Targeted Information with Twint
 How To:
Catch an Internet Catfish with Grabify Tracking Links
How To:
Catch an Internet Catfish with Grabify Tracking Links
 How To:
Discover & Attack Raspberry Pis Using Default Credentials with Rpi-hunter
How To:
Discover & Attack Raspberry Pis Using Default Credentials with Rpi-hunter
 How To:
Probe Websites for Vulnerabilities More Easily with the TIDoS Framework
How To:
Probe Websites for Vulnerabilities More Easily with the TIDoS Framework
 How To:
Scan, Fake & Attack Wi-Fi Networks with the ESP8266-Based WiFi Deauther
How To:
Scan, Fake & Attack Wi-Fi Networks with the ESP8266-Based WiFi Deauther
 How To:
Use & Abuse the Address Resolution Protocol (ARP) to Locate Hosts on a Network
How To:
Use & Abuse the Address Resolution Protocol (ARP) to Locate Hosts on a Network
 How To:
Understand & Use IPv4 to Navigate a Network
How To:
Understand & Use IPv4 to Navigate a Network
 How To:
Intercept Security Camera Footage Using the New Hak5 Plunder Bug
How To:
Intercept Security Camera Footage Using the New Hak5 Plunder Bug
 How To:
Spy on Network Relationships with Airgraph-Ng
How To:
Spy on Network Relationships with Airgraph-Ng
 How To:
Hijack Chromecasts with CATT to Display Images, Messages, Videos, Sites & More
How To:
Hijack Chromecasts with CATT to Display Images, Messages, Videos, Sites & More
 How To:
Track a Target Using Canary Token Tracking Links
How To:
Track a Target Using Canary Token Tracking Links
 How To:
Scan for Vulnerabilities on Any Website Using Nikto
How To:
Scan for Vulnerabilities on Any Website Using Nikto
 How To:
Inconspicuously Sniff Wi-Fi Data Packets Using an ESP8266
How To:
Inconspicuously Sniff Wi-Fi Data Packets Using an ESP8266
 How To:
Automate Wi-Fi Hacking with Wifite2
How To:
Automate Wi-Fi Hacking with Wifite2
 How To:
Control Anything with a Wi-Fi Relay Switch Using aRest
How To:
Control Anything with a Wi-Fi Relay Switch Using aRest
 How To:
Brute-Force Nearly Any Website Login with Hatch
How To:
Brute-Force Nearly Any Website Login with Hatch
 How To:
Intercept Images from a Security Camera Using Wireshark
How To:
Intercept Images from a Security Camera Using Wireshark
 How To:
Use Ettercap to Intercept Passwords with ARP Spoofing
How To:
Use Ettercap to Intercept Passwords with ARP Spoofing
 How To:
Take Control of Sonos IoT Devices with Python
How To:
Take Control of Sonos IoT Devices with Python
 How To:
Tactical Nmap for Beginner Network Reconnaissance
How To:
Tactical Nmap for Beginner Network Reconnaissance
 How To:
Encrypt Your Notes, Photos & Archives with EncryptPad
How To:
Encrypt Your Notes, Photos & Archives with EncryptPad
 How To:
Locate & Exploit Devices Vulnerable to the Libssh Security Flaw
How To:
Locate & Exploit Devices Vulnerable to the Libssh Security Flaw
 How To:
Enable Monitor Mode & Packet Injection on the Raspberry Pi
How To:
Enable Monitor Mode & Packet Injection on the Raspberry Pi
 How To:
Exploit Recycled Credentials with H8mail to Break into User Accounts
How To:
Exploit Recycled Credentials with H8mail to Break into User Accounts
 How To:
Check if Your Wireless Network Adapter Supports Monitor Mode & Packet Injection
How To:
Check if Your Wireless Network Adapter Supports Monitor Mode & Packet Injection
 How To:
Listen to Radio Conversations on Android with an RTL-SDR Dongle & OTG Adapter
How To:
Listen to Radio Conversations on Android with an RTL-SDR Dongle & OTG Adapter
 How to Hack Wi-Fi:
Cracking WPA2 Passwords Using the New PMKID Hashcat Attack
How to Hack Wi-Fi:
Cracking WPA2 Passwords Using the New PMKID Hashcat Attack
 How To:
Detect When a Device Is Nearby with the ESP8266 Friend Detector
How To:
Detect When a Device Is Nearby with the ESP8266 Friend Detector
 How To:
Detect & Classify Wi-Fi Jamming Packets with the NodeMCU
How To:
Detect & Classify Wi-Fi Jamming Packets with the NodeMCU
 How To:
Use an ESP8266 Beacon Spammer to Track Smartphone Users
How To:
Use an ESP8266 Beacon Spammer to Track Smartphone Users
 How To:
Uncover Hidden Subdomains to Reveal Internal Services with CT-Exposer
How To:
Uncover Hidden Subdomains to Reveal Internal Services with CT-Exposer
 How To:
Conduct OSINT Recon on a Target Domain with Raccoon Scanner
How To:
Conduct OSINT Recon on a Target Domain with Raccoon Scanner
 How To:
Use the Buscador OSINT VM for Conducting Online Investigations
How To:
Use the Buscador OSINT VM for Conducting Online Investigations
 How To:
Program a $6 NodeMCU to Detect Wi-Fi Jamming Attacks in the Arduino IDE
How To:
Program a $6 NodeMCU to Detect Wi-Fi Jamming Attacks in the Arduino IDE
 Mac for Hackers:
How to Set Up a MacOS System for Wi-Fi Packet Capturing
Mac for Hackers:
How to Set Up a MacOS System for Wi-Fi Packet Capturing
Sites
- Hot
- Latest
-
 How To:
Change a Phone's Coordinates by Spoofing Wi-Fi Geolocation Hotspots
How To:
Change a Phone's Coordinates by Spoofing Wi-Fi Geolocation Hotspots
-
 How To:
Hunt Down Wi-Fi Devices with a Directional Antenna
How To:
Hunt Down Wi-Fi Devices with a Directional Antenna
-
 How To:
Hack 5 GHz Wi-Fi Networks with an Alfa Wi-Fi Adapter
How To:
Hack 5 GHz Wi-Fi Networks with an Alfa Wi-Fi Adapter
-
 How To:
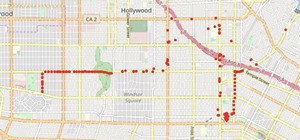
Map Wardriving Data with Jupyter Notebook
How To:
Map Wardriving Data with Jupyter Notebook
-
 How To:
Pick an Antenna for Wi-Fi Hacking
How To:
Pick an Antenna for Wi-Fi Hacking
-
 How to Hack with Arduino:
Defeat VPNs & Track a MacOS Computer Remotely
How to Hack with Arduino:
Defeat VPNs & Track a MacOS Computer Remotely
-
 How to Hack with Arduino:
Tracking Which Networks a Mac Has Connected To & When
How to Hack with Arduino:
Tracking Which Networks a Mac Has Connected To & When
-
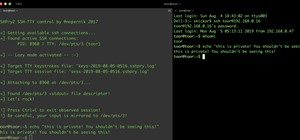
 How To:
Spy on SSH Sessions with SSHPry2.0
How To:
Spy on SSH Sessions with SSHPry2.0
-
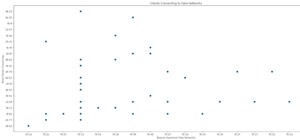
 How To:
Analyze Wi-Fi Data Captures with Jupyter Notebook
How To:
Analyze Wi-Fi Data Captures with Jupyter Notebook
-
 How to Hack with Arduino:
Building MacOS Payloads for Inserting a Wi-Fi Backdoor
How to Hack with Arduino:
Building MacOS Payloads for Inserting a Wi-Fi Backdoor
-
 How To:
Hack Wi-Fi Networks with Bettercap
How To:
Hack Wi-Fi Networks with Bettercap
-
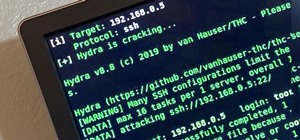
 How To:
Brute-Force SSH, FTP, VNC & More with BruteDum
How To:
Brute-Force SSH, FTP, VNC & More with BruteDum
-
 How To:
Program MicroPython NeoPixel Holiday Lights to Animate However You Want
How To:
Program MicroPython NeoPixel Holiday Lights to Animate However You Want
-
 How To:
Get Started with MicroPython for ESP8266 Microcontrollers
How To:
Get Started with MicroPython for ESP8266 Microcontrollers
-
 How To:
Crack WPA & WPA2 Wi-Fi Passwords with Pyrit
How To:
Crack WPA & WPA2 Wi-Fi Passwords with Pyrit
-
 How To:
Use Hash-Identifier to Determine Hash Types for Password Cracking
How To:
Use Hash-Identifier to Determine Hash Types for Password Cracking
-
 How To:
Spy on Traffic from a Smartphone with Wireshark
How To:
Spy on Traffic from a Smartphone with Wireshark
-
 How To:
Securely Sniff Wi-Fi Packets with Sniffglue
How To:
Securely Sniff Wi-Fi Packets with Sniffglue
-
 How To:
Hack MacOS with Digispark Ducky Script Payloads
How To:
Hack MacOS with Digispark Ducky Script Payloads
-
 How To:
Run Your Favorite Graphical X Applications Over SSH
How To:
Run Your Favorite Graphical X Applications Over SSH
-
 How to Hack Wi-Fi:
Cracking WPA2 Passwords Using the New PMKID Hashcat Attack
How to Hack Wi-Fi:
Cracking WPA2 Passwords Using the New PMKID Hashcat Attack
-
 How To:
Brute-Force Nearly Any Website Login with Hatch
How To:
Brute-Force Nearly Any Website Login with Hatch
-
 How To:
Use Kismet to Watch Wi-Fi User Activity Through Walls
How To:
Use Kismet to Watch Wi-Fi User Activity Through Walls
-
 How To:
Spy on Traffic from a Smartphone with Wireshark
How To:
Spy on Traffic from a Smartphone with Wireshark
-
 How To:
Hack Wi-Fi Networks with Bettercap
How To:
Hack Wi-Fi Networks with Bettercap
-
 How To:
Intercept Images from a Security Camera Using Wireshark
How To:
Intercept Images from a Security Camera Using Wireshark
-
 How To:
Hack 5 GHz Wi-Fi Networks with an Alfa Wi-Fi Adapter
How To:
Hack 5 GHz Wi-Fi Networks with an Alfa Wi-Fi Adapter
-
 How To:
Scan for Vulnerabilities on Any Website Using Nikto
How To:
Scan for Vulnerabilities on Any Website Using Nikto
-
 How to Hack Wi-Fi:
Stealing Wi-Fi Passwords with an Evil Twin Attack
How to Hack Wi-Fi:
Stealing Wi-Fi Passwords with an Evil Twin Attack
-
 How to Hack Wi-Fi:
Get Anyone's Wi-Fi Password Without Cracking Using Wifiphisher
How to Hack Wi-Fi:
Get Anyone's Wi-Fi Password Without Cracking Using Wifiphisher
-
 How To:
Use Ettercap to Intercept Passwords with ARP Spoofing
How To:
Use Ettercap to Intercept Passwords with ARP Spoofing
-
 How To:
Automate Wi-Fi Hacking with Wifite2
How To:
Automate Wi-Fi Hacking with Wifite2
-
 How To:
Scan, Fake & Attack Wi-Fi Networks with the ESP8266-Based WiFi Deauther
How To:
Scan, Fake & Attack Wi-Fi Networks with the ESP8266-Based WiFi Deauther
-
 How To:
Catch an Internet Catfish with Grabify Tracking Links
How To:
Catch an Internet Catfish with Grabify Tracking Links
-
 How To:
Hack WPA & WPA2 Wi-Fi Passwords with a Pixie-Dust Attack Using Airgeddon
How To:
Hack WPA & WPA2 Wi-Fi Passwords with a Pixie-Dust Attack Using Airgeddon
-
 How To:
Detect & Classify Wi-Fi Jamming Packets with the NodeMCU
How To:
Detect & Classify Wi-Fi Jamming Packets with the NodeMCU
-
 How To:
Find Vulnerable Webcams Across the Globe Using Shodan
How To:
Find Vulnerable Webcams Across the Globe Using Shodan
-
 How To:
Check if Your Wireless Network Adapter Supports Monitor Mode & Packet Injection
How To:
Check if Your Wireless Network Adapter Supports Monitor Mode & Packet Injection
-
 How To:
Find Identifying Information from a Phone Number Using OSINT Tools
How To:
Find Identifying Information from a Phone Number Using OSINT Tools
-
 How To:
Find Passwords in Exposed Log Files with Google Dorks
How To:
Find Passwords in Exposed Log Files with Google Dorks
-
 How To:
Create Custom Wordlists for Password Cracking Using the Mentalist
How To:
Create Custom Wordlists for Password Cracking Using the Mentalist
-
 How To:
Phish for Social Media & Other Account Passwords with BlackEye
How To:
Phish for Social Media & Other Account Passwords with BlackEye
-
 How To:
Hack Wi-Fi & Networks More Easily with Lazy Script
How To:
Hack Wi-Fi & Networks More Easily with Lazy Script
-
 How To:
Enable Monitor Mode & Packet Injection on the Raspberry Pi
How To:
Enable Monitor Mode & Packet Injection on the Raspberry Pi
-
 How To:
Target Bluetooth Devices with Bettercap
How To:
Target Bluetooth Devices with Bettercap
-
 How To:
Use Hash-Identifier to Determine Hash Types for Password Cracking
How To:
Use Hash-Identifier to Determine Hash Types for Password Cracking
-
 How To:
Pick an Antenna for Wi-Fi Hacking
How To:
Pick an Antenna for Wi-Fi Hacking
-
 How To:
Obtain Valuable Data from Images Using Exif Extractors
How To:
Obtain Valuable Data from Images Using Exif Extractors
-
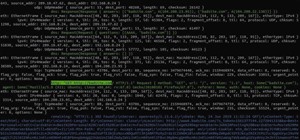
 How To:
Use MDK3 for Advanced Wi-Fi Jamming
How To:
Use MDK3 for Advanced Wi-Fi Jamming
-
 How to Hack Wi-Fi:
Hunting Down & Cracking WEP Networks
How to Hack Wi-Fi:
Hunting Down & Cracking WEP Networks
-
 How To:
Create Malicious QR Codes to Hack Phones & Other Scanners
How To:
Create Malicious QR Codes to Hack Phones & Other Scanners
-
 How to Hack Wi-Fi:
Capturing WPA Passwords by Targeting Users with a Fluxion Attack
How to Hack Wi-Fi:
Capturing WPA Passwords by Targeting Users with a Fluxion Attack
-
 How To:
Discover & Attack Raspberry Pis Using Default Credentials with Rpi-hunter
How To:
Discover & Attack Raspberry Pis Using Default Credentials with Rpi-hunter
-
 How to Hack Wi-Fi:
Disabling Security Cameras on Any Wireless Network with Aireplay-Ng
How to Hack Wi-Fi:
Disabling Security Cameras on Any Wireless Network with Aireplay-Ng
-
 How To:
Hunt Down Social Media Accounts by Usernames with Sherlock
How To:
Hunt Down Social Media Accounts by Usernames with Sherlock
-
 How To:
Hunt Down Wi-Fi Devices with a Directional Antenna
How To:
Hunt Down Wi-Fi Devices with a Directional Antenna
-
 How To:
Tactical Nmap for Beginner Network Reconnaissance
How To:
Tactical Nmap for Beginner Network Reconnaissance
-
 How To:
Use & Abuse the Address Resolution Protocol (ARP) to Locate Hosts on a Network
How To:
Use & Abuse the Address Resolution Protocol (ARP) to Locate Hosts on a Network
-
 How To:
Build a Beginner Hacking Kit with the Raspberry Pi 3 Model B+
How To:
Build a Beginner Hacking Kit with the Raspberry Pi 3 Model B+
-
 How To:
Control Network Traffic with Evil Limiter to Throttle or Kick Off Devices
How To:
Control Network Traffic with Evil Limiter to Throttle or Kick Off Devices