Hot Posts

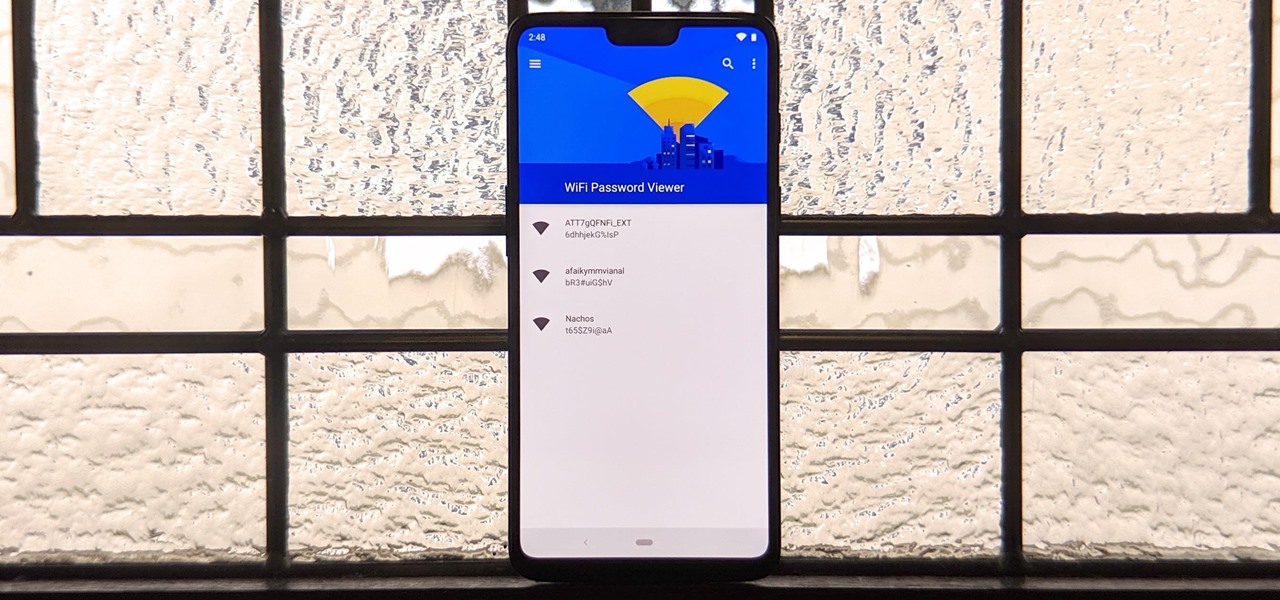
How To: See Passwords for Wi-Fi Networks You've Connected Your Android Device To
You've probably connected your Android device to dozens of Wi-Fi networks since you've had it, and your phone or tablet remembers each of them. Whether it's a hotspot at home, school, work, the gym, a coffee shop, a relative's apartment — or even from a friend's phone — each time you type in a Wi-Fi password, your Android device saves it for safekeeping and easy access later.

News: Apple Pencil 3 Is Almost Here — And It Comes with Squeeze Gestures and These Other Features
Apple's spring event, where the company will announce a new iPad model, is just around the corner. We also expect to see the long-awaited Apple Pencil (3rd generation), also known more simply as Apple Pencil 3, with several significant enhancements that promise to make it an indispensable tool for anyone who uses their iPad for note-taking, sketching, illustrating graphics, and more.

How To: Use FaceTime's Secret Hand Gestures and Reaction Buttons to Add Animated On-Screen Effects to Your Video Feed
Apple's Messages app has long had visual effects you could apply manually after long-pressing the send button, and there are even hidden keywords you could use to trigger full-screen effects automatically. FaceTime's latest update also gives you some full-screen effects to play around with during video calls, but the triggers are an entirely different concept — hand gestures.

How To: The Messaging Trick You Never Knew You Needed
Whether you're wielding an iPhone, iPad, Mac, Android phone or tablet, or even a Windows PC, this little-known secret holds the key to effortless assistance and unwavering obedience. Intrigued? I thought so.

How To: Make Spoofed Calls Using Any Phone Number You Want Right from Your Smartphone
Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to fool you into picking up. Turns out, making a spoofed call is something anybody can do — even you.
How To: Clone Any Android App on Your Samsung Galaxy Phone Without Using Any Third-Party Tools
Samsung has a cool security feature built into One UI that has an interesting side effect, one that lets you have two separate copies of any Android app on your Galaxy phone. And that's not the only integrated Samsung tool for cloning apps.

BT Recon: How to Snoop on Bluetooth Devices Using Kali Linux
While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

Warning: Sensitive Info You Black Out in Images Can Be Revealed with a Few Quick Edits on Your iPhone
These days, most images we post online or share with others come from our smartphones. Whenever personal data is in them, such as debit card numbers, addresses, phone numbers, passwords, and other sensitive information, it's easy to jump into your iPhone's markup tools to black out the text before sharing. But a digital marker may not hide everything.

How To: Dox Anyone
Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...

How To: Make Siri Say Whatever You Want Every Time You Connect Your iPhone to a Charger
Whenever your iPhone's ringer is on, you'll hear Apple's iconic "Connect Power" chime every time you connect it to a wired or wireless power source, which lets you know that charging has started. There's no way to disable the sound without turning on Silent mode, but there is a way to make Siri automatically say whatever you want after a successful connection.

How To: Create and Use Collaborative Playlists on Apple Music with Your Friends (Works on iPhone, Android, and More)
Collaboration is available in many different Apple apps, from Notes and Reminders to Photos, Freeform, and even Files. Now you can add to the list Apple Music, which will let you collaborate on playlists with friends.
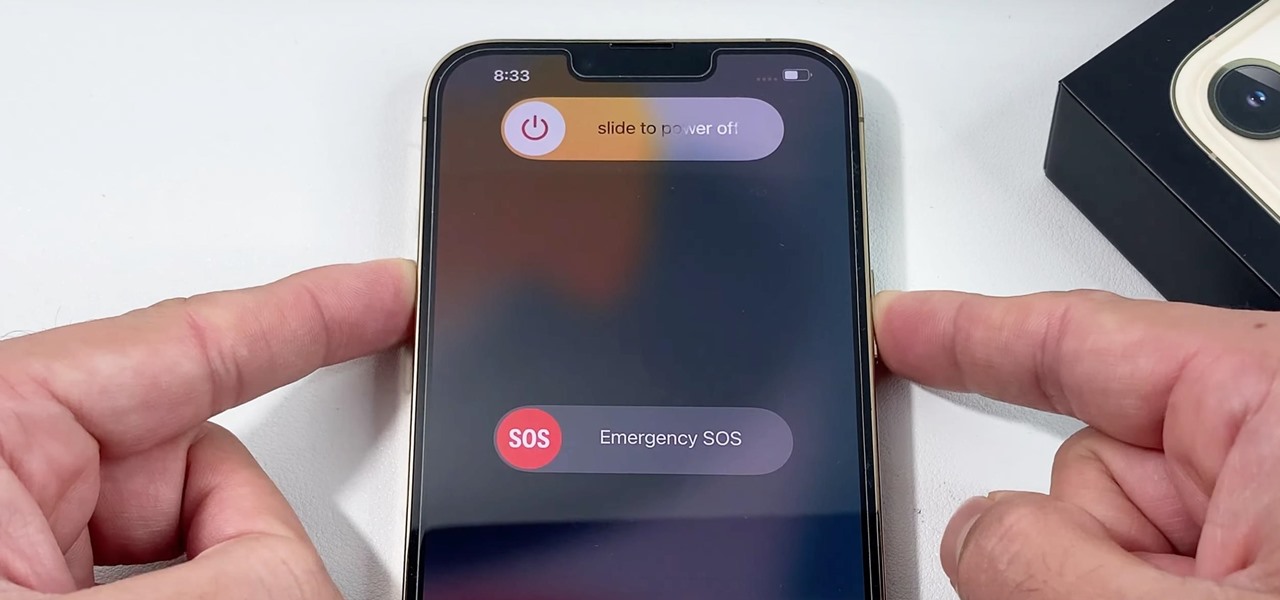
How To: 8 Ways to Shut Down and Restart Your iPhone 13, 13 Mini, 13 Pro, or 13 Pro Max
There are multiple ways to turn your iPhone 13, 13 mini, 13 Pro, or 13 Pro Max on and off, but it can be confusing because those ways will either shut down, power on, restart, or force restart the device.

How To: The Paranoid Mac Owner's Guide to Defeating Remote Snooping & Evil Maid Attacks
If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

How To: Keep Your Night Vision Sharp with the iPhone's Hidden Red Screen
Night Shift, Dark Mode, Reduce White Point, and Zoom's Low Light Filter all help reduce the harmful effects on your body's clock that bright iPhone and iPad screens have at night. But there's another option on iOS and iPadOS that turns your entire display red, and it's useful for so much more than just late-night browsing in bed.
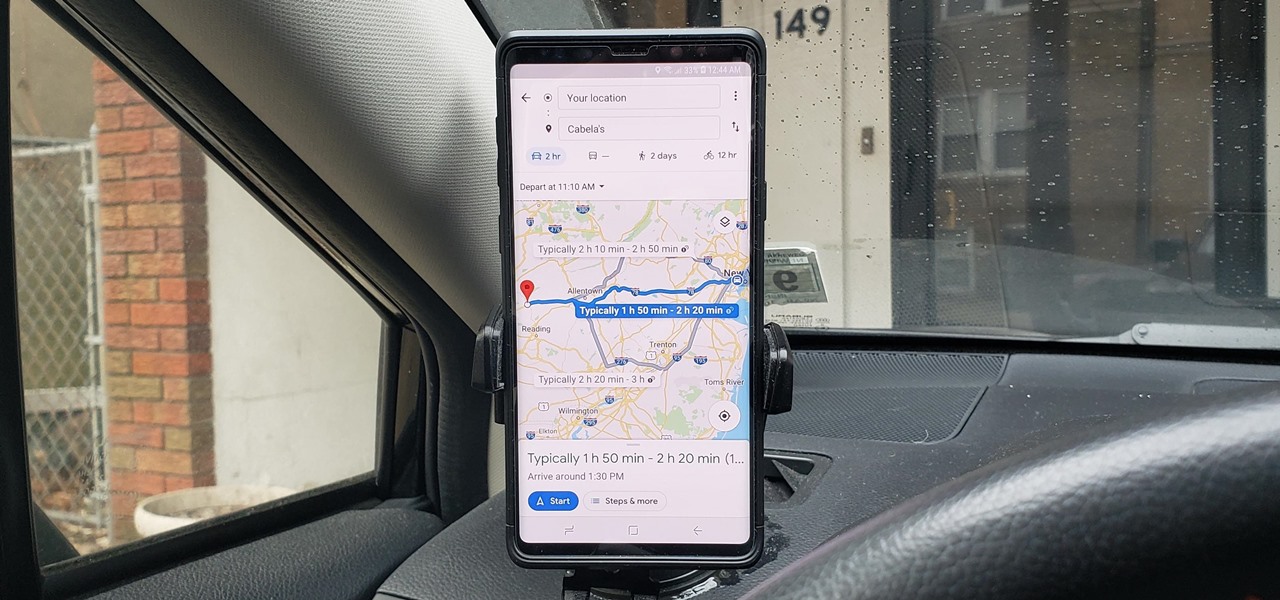
How To: See What Traffic Will Be Like at a Specific Time with Google Maps
As intuitive as Google Maps is for finding the best routes, it never let you choose departure and arrival times in the mobile app. This feature has long been available on the desktop site, allowing you to see what traffic should be like at a certain time and how long your drive would take at a point in the future. Fortunately, Google has finally added this feature to the app for iPhone and Android.
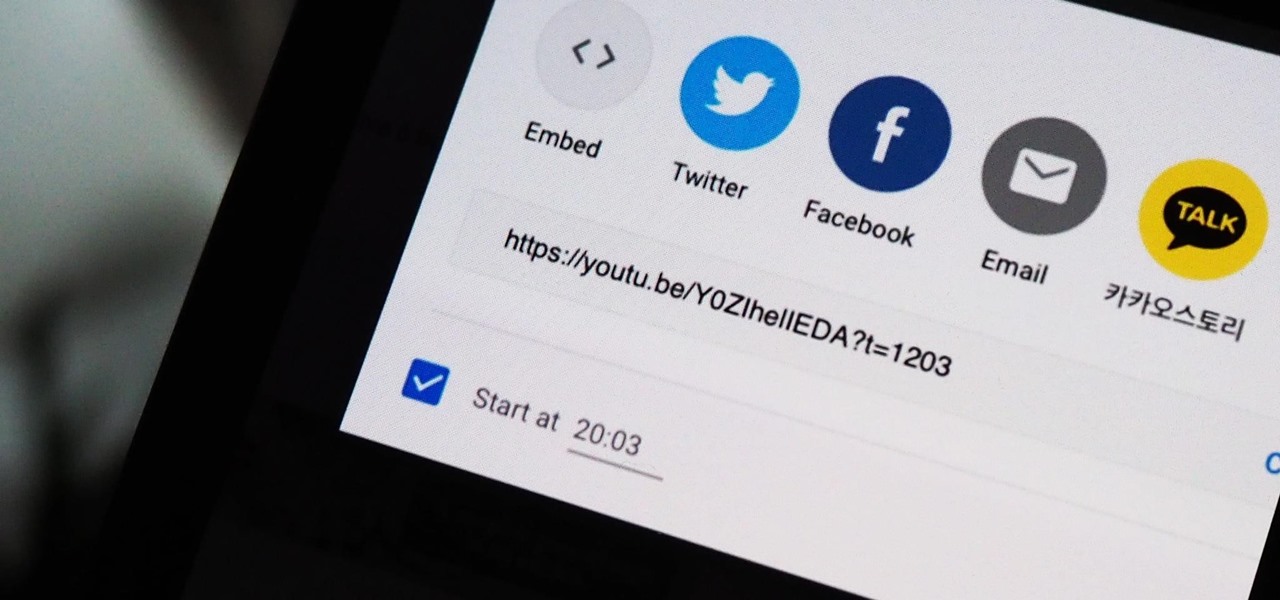
How To: The Trick That Lets You Link to Specific Start Times in YouTube Videos Right from Your Phone
You can add a timestamp to any YouTube video in just a few clicks from the desktop website on your computer but not from YouTube's iOS or Android app. Until YouTube adds a "start time" when sharing videos from the mobile app, you'll have to use one of these workarounds on your phone or tablet.

How To: Crack Password-Protected Microsoft Office Files, Including Word Docs & Excel Spreadsheets
Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.

How To: Crack Shadow Hashes After Getting Root on a Linux System
After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

How To: Find Vulnerable Webcams Across the Globe Using Shodan
Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.
How To: 27 New Features and Changes Coming to Your iPhone with iOS 17.5
Apple released iOS 17.4 on March 5 with over 30 new features, but now it's iOS 17.5's turn for the spotlight. The update, currently in beta, gives us a few interesting updates and changes for iPhone, including a new word game, and there's even a sneak peek at what could be coming in the stable build.
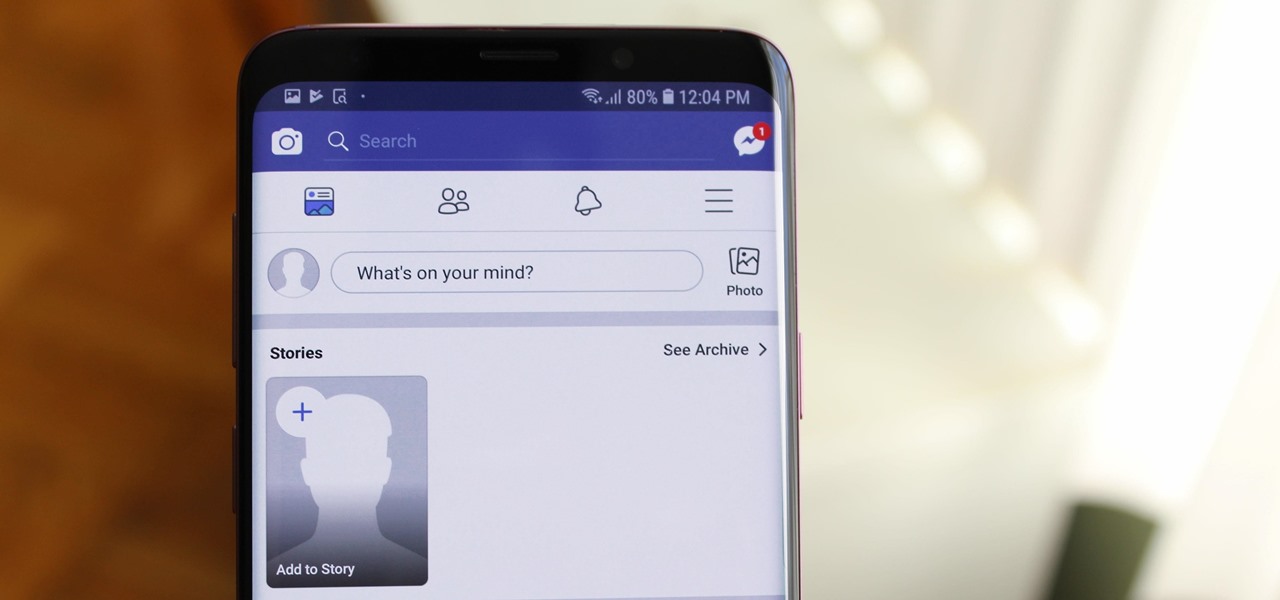
How To: Hide Stories in Your Facebook Feed on iPhone or Android
When Facebook introduced Stories in 2017, many users despised the Snapchat-like feature on their main page. However, despite the outcry, Facebook doesn't plan to let you remove it. But you don't have settle for this. With the help of some third-party apps, you no longer have to deal with Stories.

How To: Hack Apache Tomcat via Malicious WAR File Upload
Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

How To: Find Identifying Information from a Phone Number Using OSINT Tools
Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.
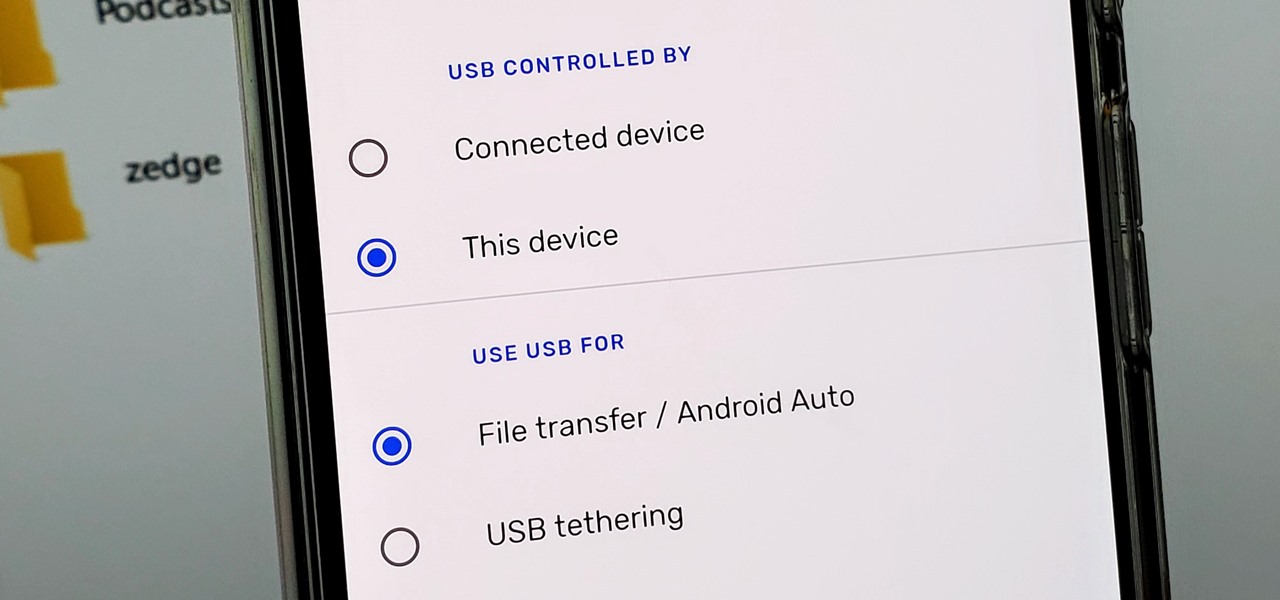
How To: Make the USB Connection on Your Android Phone Default to File Transfer Mode
Back in the earlier days of Android, you were able to connect your phone to a computer, and it would mount automatically. This meant once the USB connection was made, your internal storage would pop up on the computer and you could go about your business. But recent versions of Android changed that to help increase security.

How To: The Easiest Way to Secretly Record Someone's Conversation with Your iPhone
Your iPhone's built-in Voice Memos app is a great way to record the audio around you, whether it be conversations, lectures, meetings, interviews, discussions, chitchat, gossip, or other kinds of talks. But if your goal is to record audio on the down-low without being noticed, you'll need to know the hidden shortcut.

How To: Use Ettercap to Intercept Passwords with ARP Spoofing
ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.
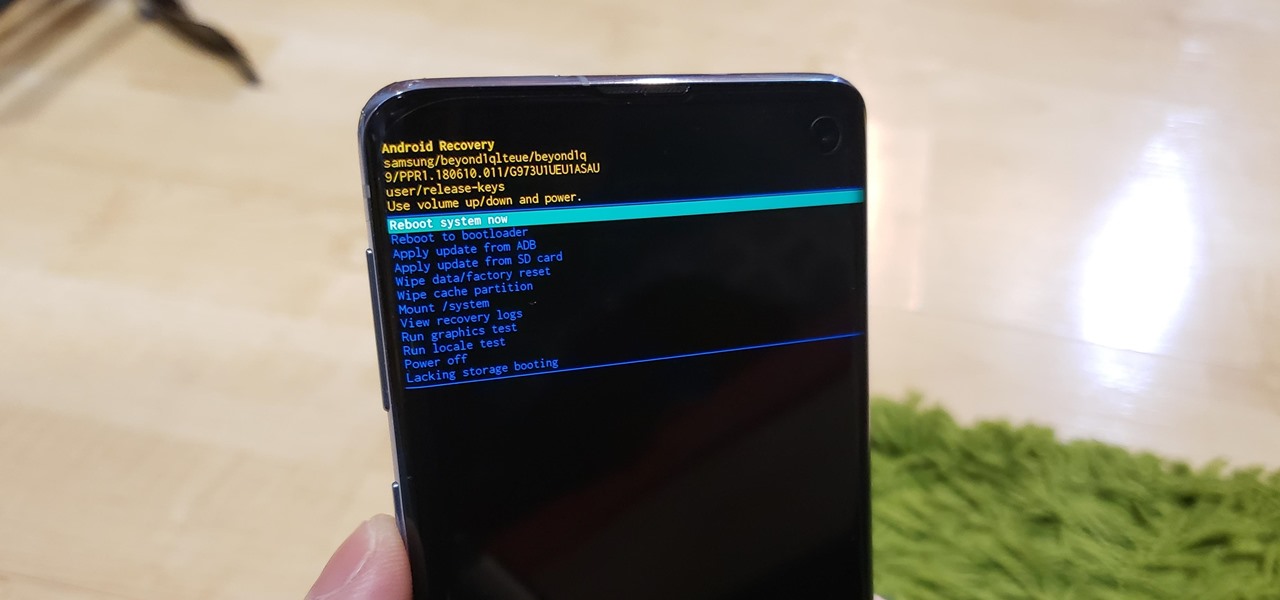
How To: Boot Your Galaxy S10 into Recovery Mode & Download Mode
You don't need to be a hardcore modder to know the importance of booting your S10 into either recovery mode or download mode. In fact, these pre-boot menus are something everyone should be familiar with. The former can help you get out of soft bricks, while the latter lets you use utilities like Odin and Smart Switch to flash firmware files and fix your phone when all other solutions fail.
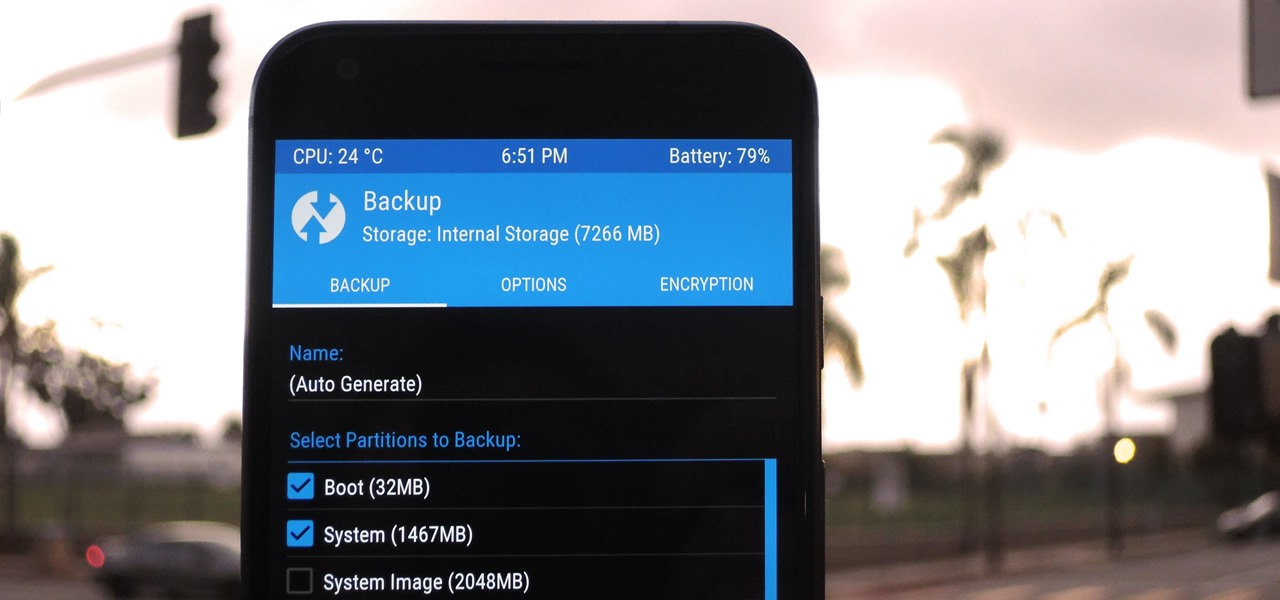
TWRP 101: How to Make a NANDroid Backup & Restore Your Entire Phone
A custom recovery is a very powerful tool. You can flash ZIPs that modify your Android device in ways that not even root can accomplish, and of course you can use it to install custom ROMs. But when you're applying all of these cool mods, there's always a chance that something could go wrong, and you might even end up bricking your device.

How To: Your iPhone Has a Hidden Text-to-Speech Tool That'll Read Articles, Books, News, and Other Text Out Loud to You
You may prefer reading news stories, web articles, and books on your iPhone over listening to them in spoken form. Still, sometimes it's necessary when driving, walking, cycling, cleaning, working, or performing other activities requiring a little multitasking. To help you out, Apple has a text-to-speech service on your iPhone — you just need to know how to find and set it up.
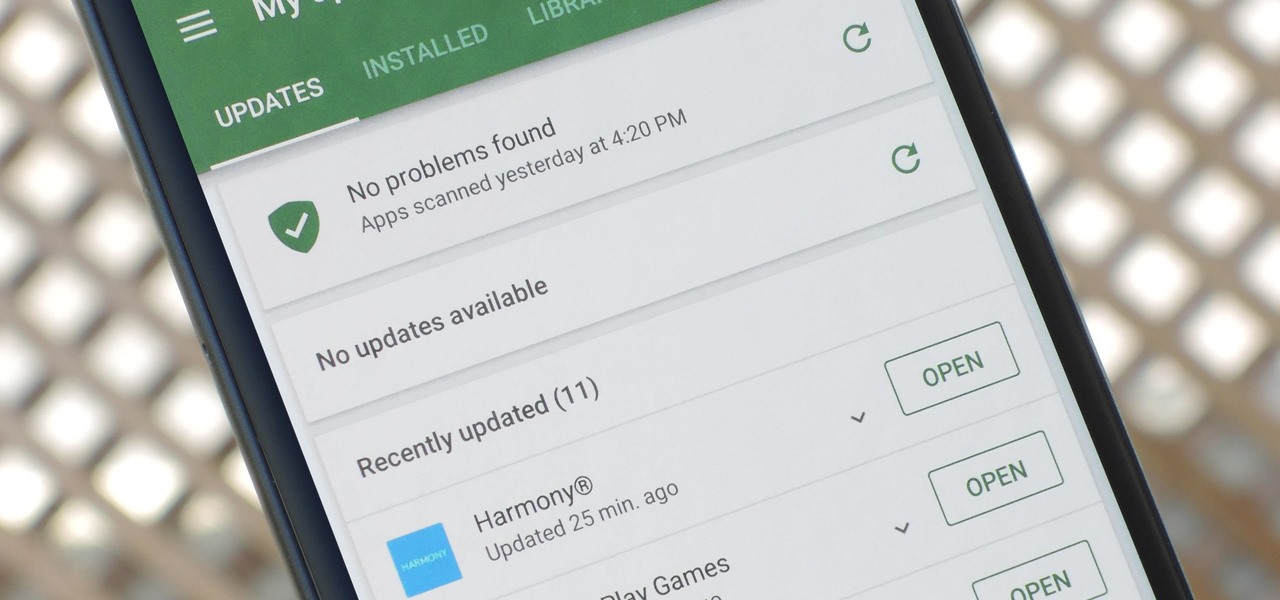
How To: Permanently Stop Any App from Updating on the Play Store — No Computer Needed
App updates bring new functionality, but they can also break old features or introduce changes no one wants. Unfortunately, if you're holding onto an older app version because you don't want to accept the update, it becomes a lot harder to keep the rest of your apps updated.

How To: Use SpiderFoot for OSINT Gathering
During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

How To: Skip the Oven—Microwave Your Fish
Fish are delicate, flaky, and can be damn tricky to cook; more often than not, you end up with a hard, dry block of flesh that makes your taste buds sad. And the best ways to cook fish that you know of—c'mon, who doesn't love a fried fish—take way too much effort for you to bother with on a weeknight. Or maybe you're looking for a healthier way to enjoy fish that doesn't require batter or frying at all.

How To: Create a Hidden Piston Door in Minecraft
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.
How To: Use the Built-in Document Scanner on Your Google Pixel
Document scanning is possible via the Google Drive app, but my brain doesn't think of opening a cloud storage app to scan a document. I usually just open the camera app and take a picture instead — and apparently, I'm not the only one.
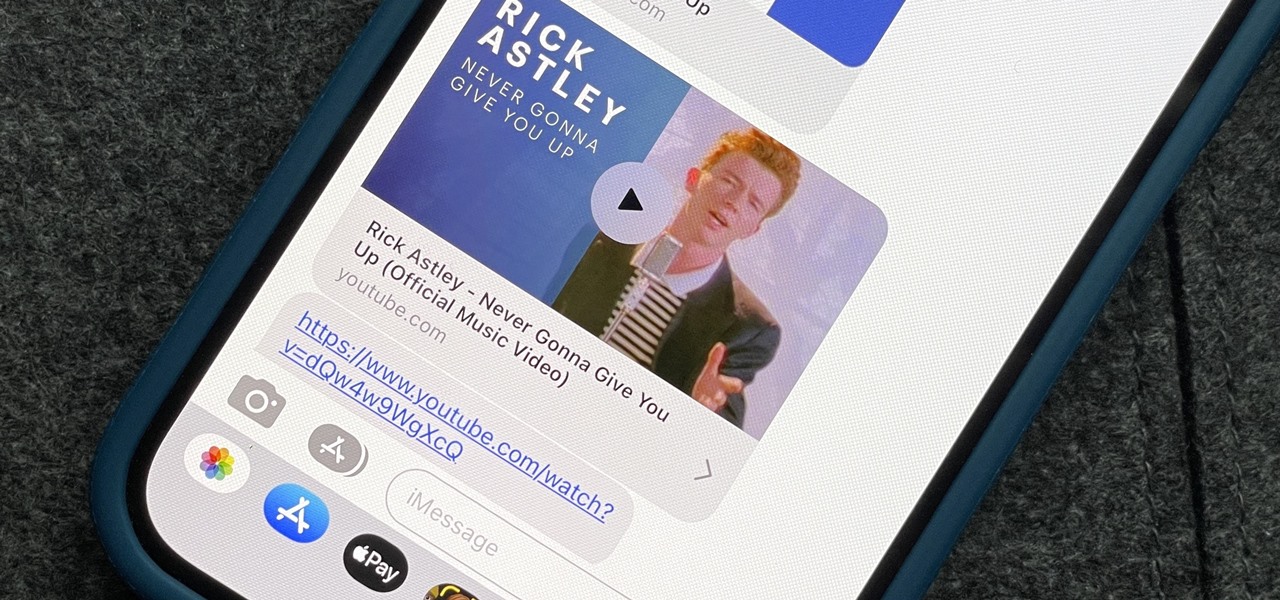
How To: The Trick to Disabling Link Previews for URLs in Your iPhone's Messages App
Apple automatically converts most URLs in the Messages app into rich link previews, but they aren't always pretty, and sometimes you just want to see the full URL instead. While there is no setting on iOS, iPadOS, or macOS that disables rich link previews in the Messages app, there is an easy way to show the URL complete with the scheme, domain name, and path.

How to Hack Wi-Fi: Cracking WPA2-PSK Passwords with Cowpatty
Welcome, my hacker novitiates! As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords. In my last post, we cracked WPA2 using aircrack-ng. In this tutorial, we'll use a piece of software developed by wireless security researcher Joshua Wright called cowpatty (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords, so let's get to it!

How To: The Ultimate Guide to Using TWRP: The Only Custom Recovery You'll Ever Need
Just the fact that you own an Android device means you're privy to an entire world of third-party development. Many of the mods you'll see here on Gadget Hacks can be performed fresh out of the box, but with root and Xposed, the list grows longer. But to truly be able to take advantage of all that Android's massive development community has to offer, you'll need to have a custom recovery installed.
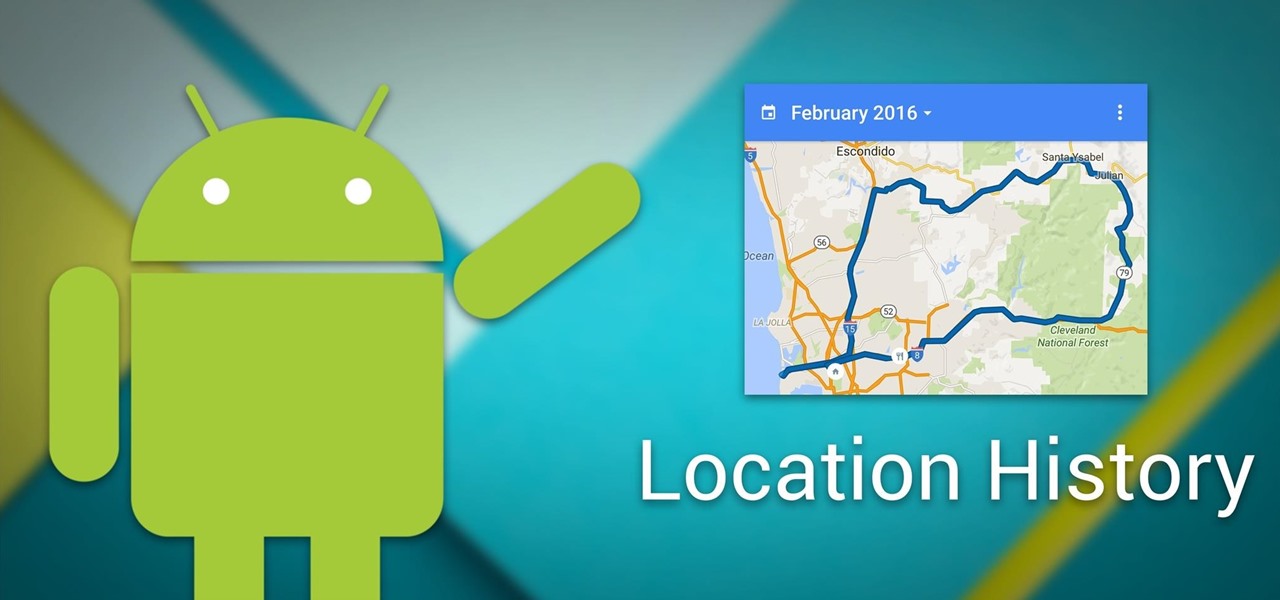
Android Basics: How to View Your Location History
Your smartphone has a GPS chip inside of it that can pinpoint your location down to the nearest 4 meters, and this little device stays in your pocket or purse all day. Combine those two facts and you start to realize that your phone knows exactly where you've been during every moment that has passed since you've owned it.

How To: Install the Real Wordle Game on Your Phone — Not a Fake Wordle Clone
Wordle has been popping up all over in the app stores, but none of them are the real Wordle. The popular word game app has amassed two million users since its launch in November 2021 but has no plans to hit the iOS App Store or Play Store any time soon — but you can still install the official Wordle app on the Home screen of your iPhone or Android phone.

How To: Knot a Hermès Scarf in 21 Different Ways
Hermès is all about giving out the free goodies—this week I posted a tutorial for making your own papercraft "Kelly bag" and for years now they've created "knotting cards", a set of DIY illustrations presenting different ways to wear their iconic scarves.






