Hot Posts

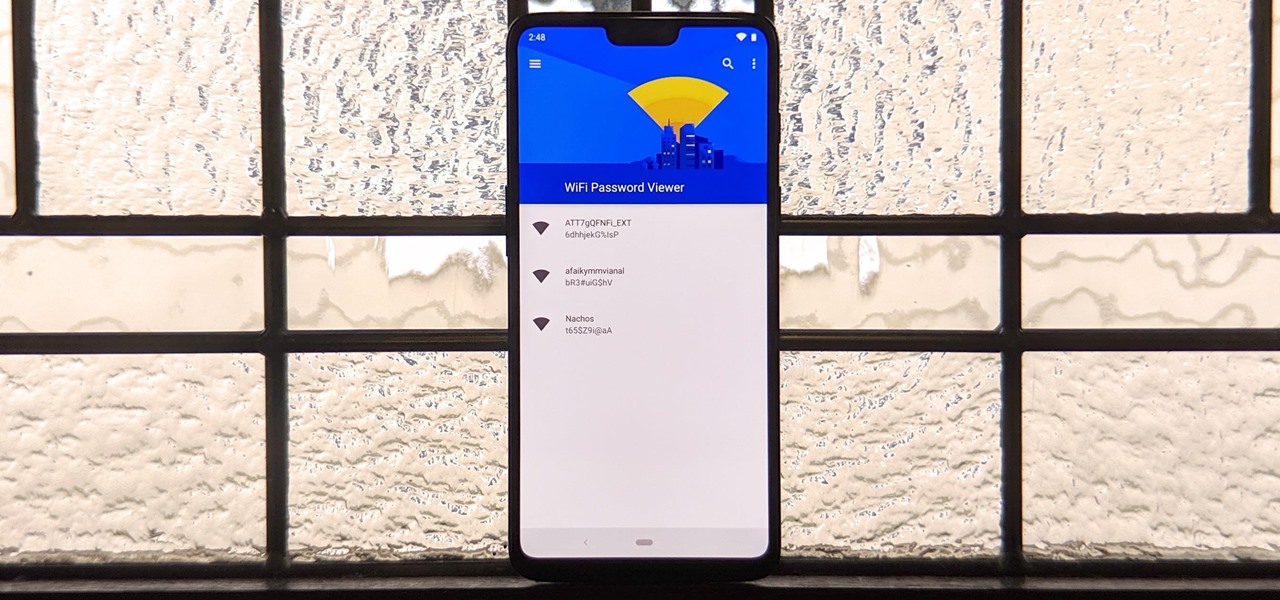
How To: See Passwords for Wi-Fi Networks You've Connected Your Android Device To
You've probably connected your Android device to dozens of Wi-Fi networks since you've had it, and your phone or tablet remembers each of them. Whether it's a hotspot at home, school, work, the gym, a coffee shop, a relative's apartment — or even from a friend's phone — each time you type in a Wi-Fi password, your Android device saves it for safekeeping and easy access later.
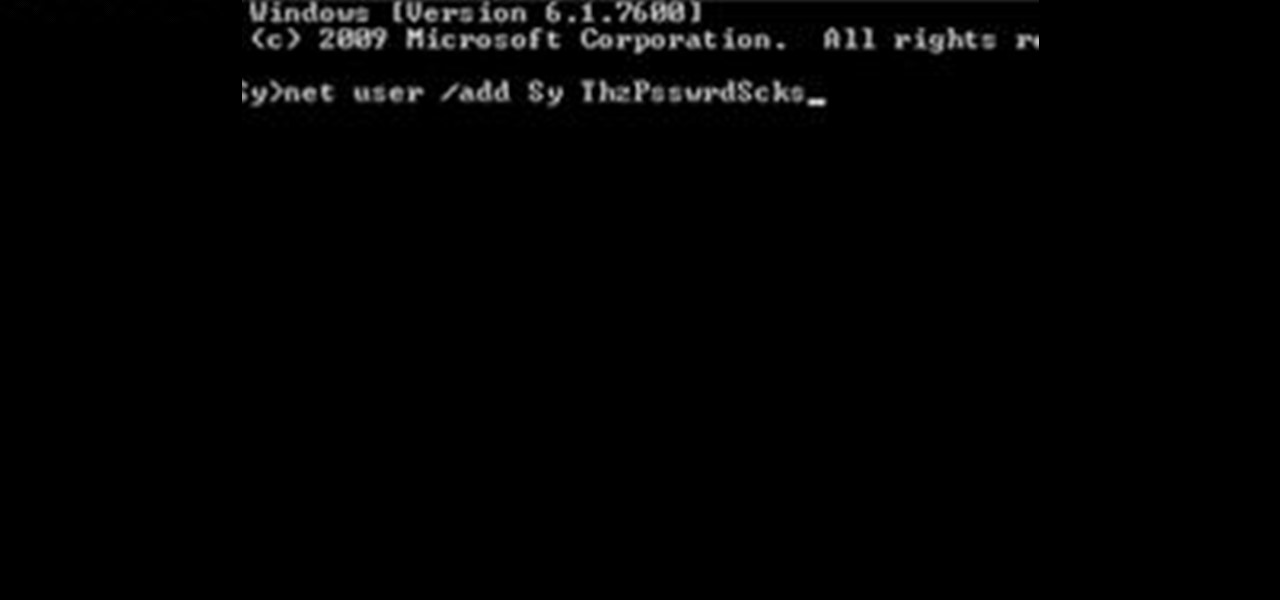
How To: Create an Admin User Account Using CMD Prompt (Windows)
This is a quick tutorial on how to create a new administrator account on a Windows computer. Step 1: Open CMD Prompt...

How To: The Messaging Trick You Never Knew You Needed
Whether you're wielding an iPhone, iPad, Mac, Android phone or tablet, or even a Windows PC, this little-known secret holds the key to effortless assistance and unwavering obedience. Intrigued? I thought so.

News: Apple Pencil 3 Is Almost Here — And It Comes with Squeeze Gestures and These Other Features
Apple's spring event, where the company will announce a new iPad model, is just around the corner. We also expect to see the long-awaited Apple Pencil (3rd generation), also known more simply as Apple Pencil 3, with several significant enhancements that promise to make it an indispensable tool for anyone who uses their iPad for note-taking, sketching, illustrating graphics, and more.
How To: Clone Any Android App on Your Samsung Galaxy Phone Without Using Any Third-Party Tools
Samsung has a cool security feature built into One UI that has an interesting side effect, one that lets you have two separate copies of any Android app on your Galaxy phone. And that's not the only integrated Samsung tool for cloning apps.

How To: Gain SSH Access to Servers by Brute-Forcing Credentials
SSH is one of the most common protocols in use in modern IT infrastructures, and because of this, it can be a valuable attack vector for hackers. One of the most reliable ways to gain SSH access to servers is by brute-forcing credentials. There are a few methods of performing an SSH brute-force attack that will ultimately lead to the discovery of valid login credentials.

How To: The Top 80+ Websites Available in the Tor Network
There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

How To: Crack Shadow Hashes After Getting Root on a Linux System
After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

How To: Find Vulnerable Webcams Across the Globe Using Shodan
Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

How To: Fix the Worn Out Heel Linings in Your Ragged Shoes & Sneakers—MacGyver Style!
The worst thing about running shoes is that they're expensive, but you're supposed to abuse them. Even if you're not a runner, everyday wear and tear takes its toll. No matter how well you take care of them, if you use them enough, they're eventually going to wind up looking like this: And it's not just running shoes. I have a pair of Vans that I've worn for almost four years, and the heels are just about ripped all the way through.
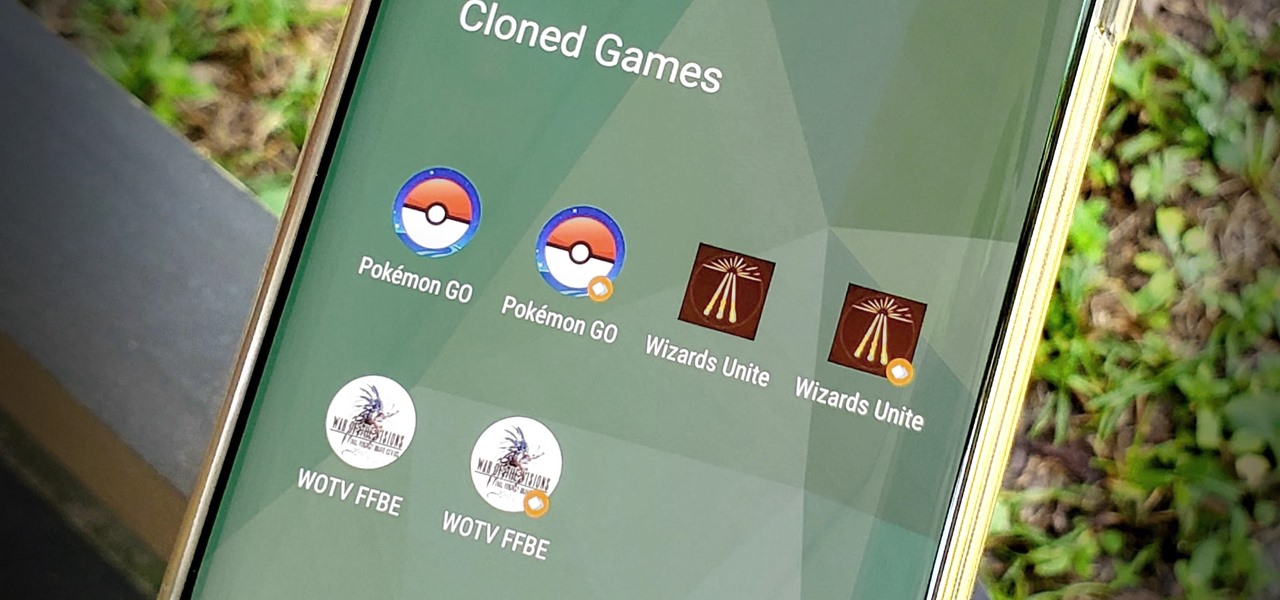
How To: Make Any App Work with OnePlus' Parallel Apps Feature
OnePlus offers a variety of features that you don't get with some other Android phones. Parallel Apps is one of those standout extras you didn't know you might enjoy until you've tried it. It allows you to clone compatible apps installed on your device, which means you can use the same app with two different accounts, for example.

How To: Use FaceTime's Secret Hand Gestures and Reaction Buttons to Add Animated On-Screen Effects to Your Video Feed
Apple's Messages app has long had visual effects you could apply manually after long-pressing the send button, and there are even hidden keywords you could use to trigger full-screen effects automatically. FaceTime's latest update also gives you some full-screen effects to play around with during video calls, but the triggers are an entirely different concept — hand gestures.
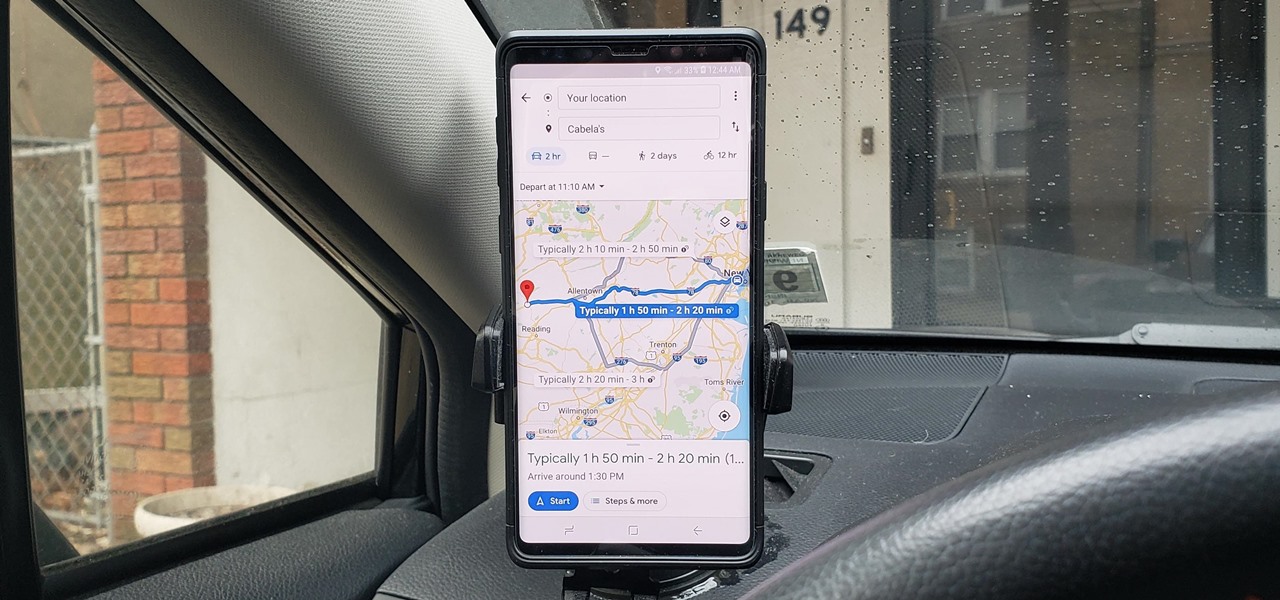
How To: See What Traffic Will Be Like at a Specific Time with Google Maps
As intuitive as Google Maps is for finding the best routes, it never let you choose departure and arrival times in the mobile app. This feature has long been available on the desktop site, allowing you to see what traffic should be like at a certain time and how long your drive would take at a point in the future. Fortunately, Google has finally added this feature to the app for iPhone and Android.
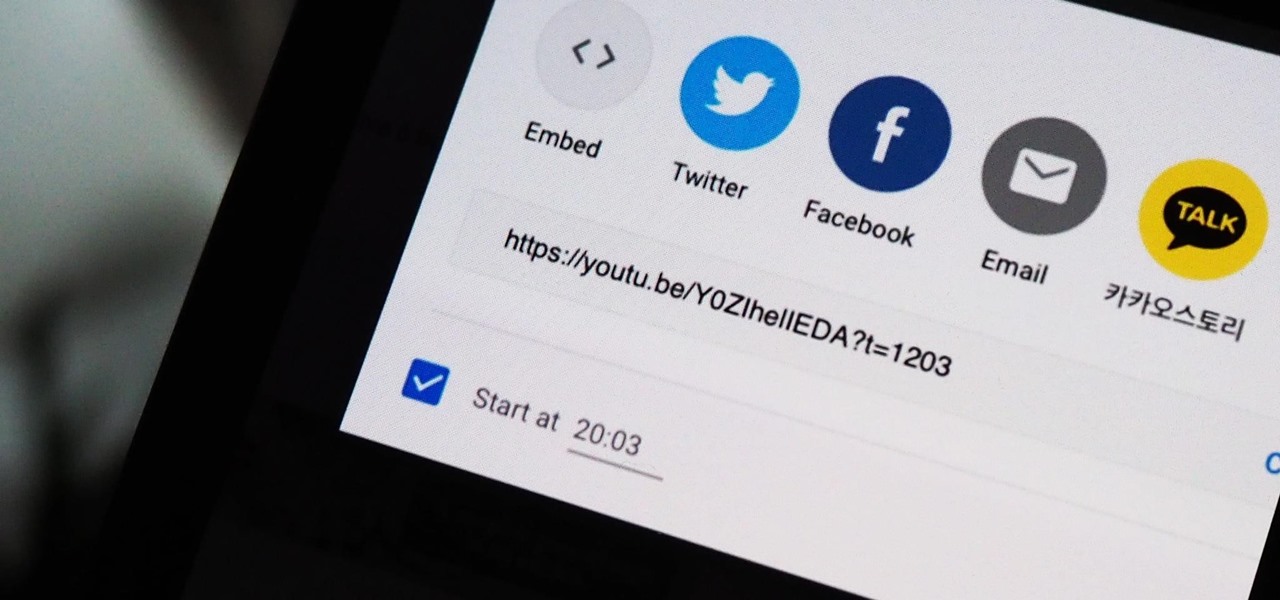
How To: The Trick That Lets You Link to Specific Start Times in YouTube Videos Right from Your Phone
You can add a timestamp to any YouTube video in just a few clicks from the desktop website on your computer but not from YouTube's iOS or Android app. Until YouTube adds a "start time" when sharing videos from the mobile app, you'll have to use one of these workarounds on your phone or tablet.

How To: Crack SSH Private Key Passwords with John the Ripper
Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

How To: Exploit EternalBlue on Windows Server with Metasploit
Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

How To: Scan for Vulnerabilities on Any Website Using Nikto
Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

How To: Brute-Force FTP Credentials & Get Server Access
Hackers often find fascinating files in the most ordinary of places, one of those being FTP servers. Sometimes, luck will prevail, and anonymous logins will be enabled, meaning anyone can just log in. But more often than not, a valid username and password will be required. But there are several methods to brute-force FTP credentials and gain server access.

BT Recon: How to Snoop on Bluetooth Devices Using Kali Linux
While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

How To: Remove Unnecessary Profiles & Certificates on Your iPhone to Protect Your Privacy & Security
When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving it much thought. This can lead to malicious software running on your iPhone, software you'll want to get rid of asap.

How To: Gain Control of WordPress by Exploiting XML-RPC
WordPress did not become what is arguably the most popular blogging and CMS platform on the planet because it was difficult to use. Rather, its user-friendly and rich feature set led to it finding a home on somewhere north of 70 million websites—and that's just counting blogs hosted on WordPress.com.

How To: Stay as Anonymous as Possible Online
There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

How To: Dox Anyone
Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...

Warning: Sensitive Info You Black Out in Images Can Be Revealed with a Few Quick Edits on Your iPhone
These days, most images we post online or share with others come from our smartphones. Whenever personal data is in them, such as debit card numbers, addresses, phone numbers, passwords, and other sensitive information, it's easy to jump into your iPhone's markup tools to black out the text before sharing. But a digital marker may not hide everything.

How To: Make This Amazing 9-Layer Density Tower from Things Found in Your Kitchen
Ralph Waldo Emerson once observed that "the seed of science" was "wonder," and taking a look at this nine-layer liquid tower from Steve Spangler's Sick Science! channel, one can't help but do just that — wonder. How is this possible? Is this magic or what?

How To: The Easiest Way to Secretly Record Someone's Conversation with Your iPhone
Your iPhone's built-in Voice Memos app is a great way to record the audio around you, whether it be conversations, lectures, meetings, interviews, discussions, chitchat, gossip, or other kinds of talks. But if your goal is to record audio on the down-low without being noticed, you'll need to know the hidden shortcut.

Gaslighting 101: How to Turn People's Own Thoughts Against Them
This is evil and it destroys people. Let's just get that out of the way. Nonetheless, suppose you need to make someone distrust their own memory and perception of reality. Suppose you want someone to believe in you more than they believe in themselves.

How to Hack Wi-Fi: Stealing Wi-Fi Passwords with an Evil Twin Attack
While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.
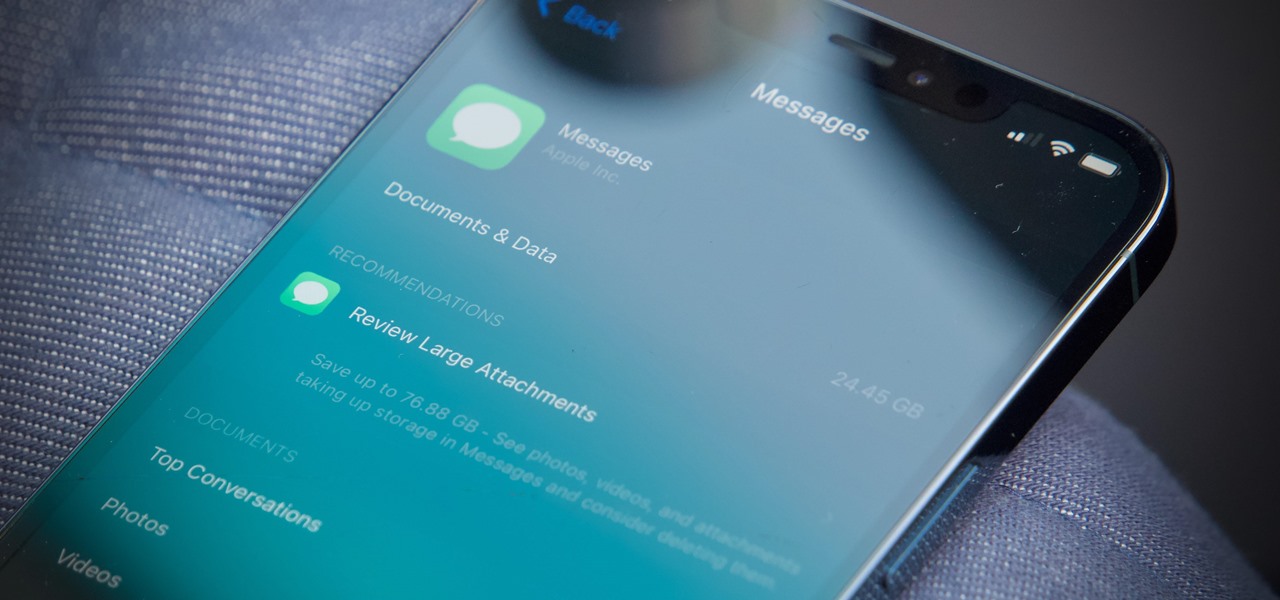
How To: If 'Messages' Consumes Too Much iPhone or iCloud Storage, Don't Delete Your Conversations Just Yet
When iOS starts barking at you that you've run out of iCloud or iPhone storage, a quick trip to your settings to see what the culprit is may show that Messages is one of the worst offenders. But if deleting message after message doesn't free up your storage much, it's likely because "Messages" doesn't really mean messages.

Android Basics: How to See What Kind of Processor You Have (ARM, ARM64, or x86)
Starting with the release of Android Lollipop, the process of installing the Xposed Framework got a bit more complicated. Not only are there separate installers for each Android version, but now, you also need to know exactly what type of processor is in your device to make sure you're downloading the right files. In fact, CPU architecture is becoming a factor in more and more scenarios these days, including certain sideloaded app updates and, of course, custom ROMs.
How To: Can't Find an App on Your iPhone's Home Screen? Its Icon Is Likely Hiding from You
You know that you have the Gmail app on your iPhone. After all, you get Gmail notifications, you see it in the app switcher, it's in the Settings app, and there's an "Open" button in the App Store instead of "Get" or a download icon. But you cannot find the app on your Home Screen. If this situation sounds like something you're dealing with on iOS 14 or iOS 15, there's an easy answer.

Hacking Windows 10: How to Dump NTLM Hashes & Crack Windows Passwords
Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

How To: Set Up Wireless Debugging on Android 11 to Send ADB Commands Without a USB Cable
From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

How To: Stealthfully Sniff Wi-Fi Activity Without Connecting to a Target Router
Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

How To: Turn Your Samsung Galaxy Smartphone or Tablet into a Second Display for Your Computer
An iPad can serve as a second screen for a Mac via Sidecar, available since iPadOS 13, but Apple isn't the only manufacturer to support such a feature. Samsung has had a similar tool since One UI 3.1 that lets you turn certain Samsung Galaxy tablets into second displays for your PC — and there's a hidden feature that expands it to more tablets and even Samsung Galaxy smartphones.

How To: Turn GIFs into Live Photos on Your iPhone
If you've ever wanted to turn your favorite GIF into a live wallpaper for your iPhone or even just make it a 3D Touch-friendly Live Photo that you can share, there's a super simple way to do so.

How to Hack Wi-Fi: Cracking WPA2-PSK Passwords Using Aircrack-Ng
Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

Magisk 101: How to Install Magisk & Root with TWRP
There are a few different ways to install Magisk. If you're already rooted and you just want access to Magisk modules, you can use Magisk Manager to install the Magisk framework. Or, if you want to pass SafetyNet on a rooted device, you can switch from SuperSU to Magisk SU. But the best way to do it is to start fresh by installing Magisk on a non-rooted phone using TWRP.

How To: Extract Bitcoin Wallet Addresses & Balances from Websites with SpiderFoot CLI
While there are completely legitimate reasons to use Bitcoin, it's also used by terrorists, drug dealers, and other shady people that need to be investigated. That's where SpiderFoot comes in, which has a command-line interface to search for Bitcoin wallet addresses on a website and query the balances associated with them.

How To: Spot a Liar Through Text Messages
While text messaging has become one of the most frequent ways we communicate with our friends, the missing body language, tone of voice, and eye contact can make it difficult to tell when someone is being dishonest. That said, it's not impossible. There are a number of subtle hints you can train yourself to recognize that will to help you detect written lies hiding in your SMS and iMessages. Here's what you should look out for.







