About Retia
- Location: Los Angeles
Retia's Popular Posts
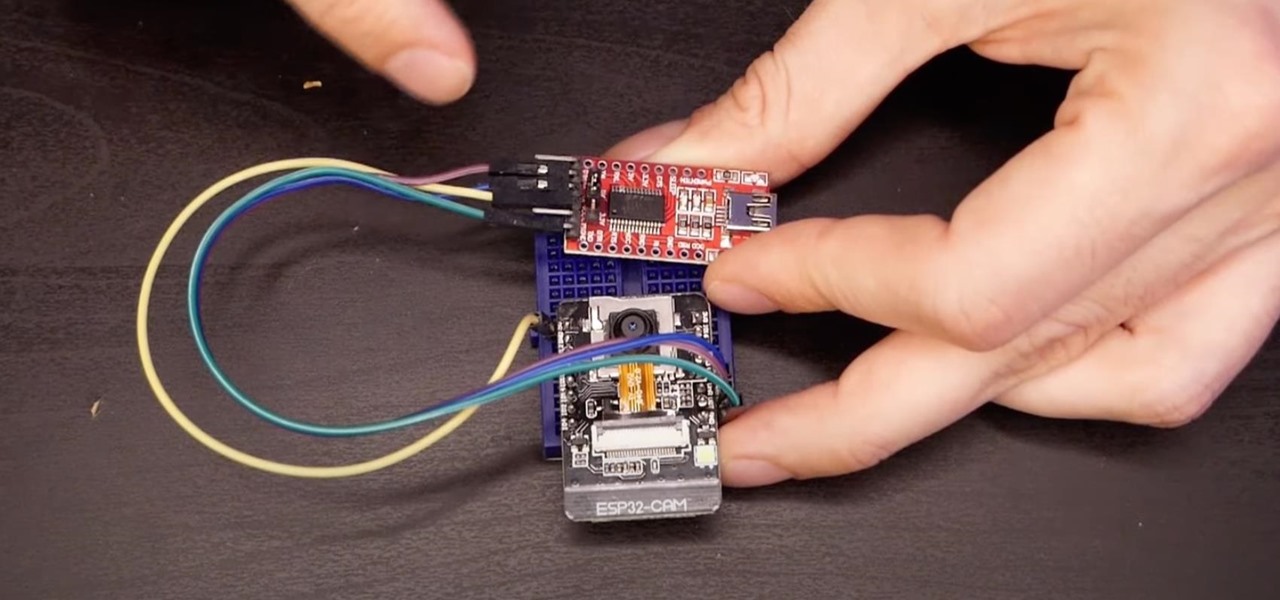 How To:
Set Up a Wi-Fi Spy Camera with an ESP32-CAM
How To:
Set Up a Wi-Fi Spy Camera with an ESP32-CAM
 How To:
Use Upip to Load MicroPython Libraries onto a Microcontroller Over Wi-Fi
How To:
Use Upip to Load MicroPython Libraries onto a Microcontroller Over Wi-Fi
 How To:
Extract Bitcoin Wallet Addresses & Balances from Websites with SpiderFoot CLI
How To:
Extract Bitcoin Wallet Addresses & Balances from Websites with SpiderFoot CLI
 How To:
Perform Advanced Man-in-the-Middle Attacks with Xerosploit
How To:
Perform Advanced Man-in-the-Middle Attacks with Xerosploit
 How To:
There Are Hidden Wi-Fi Networks All Around You — These Attacks Will Find Them
How To:
There Are Hidden Wi-Fi Networks All Around You — These Attacks Will Find Them
 How To:
Conduct Wireless Recon on Bluetooth, Wi-Fi & GPS with Sparrow-wifi
How To:
Conduct Wireless Recon on Bluetooth, Wi-Fi & GPS with Sparrow-wifi
 How To:
Generate Crackable Wi-Fi Handshakes with an ESP8266-Based Test Network
How To:
Generate Crackable Wi-Fi Handshakes with an ESP8266-Based Test Network
 How To:
Install Kali Linux as a Portable Live USB for Pen-Testing & Hacking on Any Computer
How To:
Install Kali Linux as a Portable Live USB for Pen-Testing & Hacking on Any Computer
 How To:
Unlock Facial Detection & Recognition on the Inexpensive ESP32-Based Wi-Fi Spy Camera
How To:
Unlock Facial Detection & Recognition on the Inexpensive ESP32-Based Wi-Fi Spy Camera
 How To:
Analyze Web Browser Extensions for Possible Malware & Other Malicious Activity
How To:
Analyze Web Browser Extensions for Possible Malware & Other Malicious Activity
 How To:
Hack Networks & Devices Right from Your Wrist with the Wi-Fi Deauther Watch
How To:
Hack Networks & Devices Right from Your Wrist with the Wi-Fi Deauther Watch
 How To:
Write Your Own Bash Scripts to Automate Tasks on Linux
How To:
Write Your Own Bash Scripts to Automate Tasks on Linux
 How To:
Find OSINT Data on License Plate Numbers with Skiptracer
How To:
Find OSINT Data on License Plate Numbers with Skiptracer
 How To:
Play Wi-Fi Hacking Games Using Microcontrollers to Practice Wi-Fi Attacks Legally
How To:
Play Wi-Fi Hacking Games Using Microcontrollers to Practice Wi-Fi Attacks Legally
 How To:
Build an Off-Grid Wi-Fi Voice Communication System with Android & Raspberry Pi
How To:
Build an Off-Grid Wi-Fi Voice Communication System with Android & Raspberry Pi
 How To:
Get an Internet Connection in the Middle of Nowhere to Hack Remotely
How To:
Get an Internet Connection in the Middle of Nowhere to Hack Remotely
 How To:
Null Byte's Hacker Guide to Buying an ESP32 Camera Module That's Right for Your Project
How To:
Null Byte's Hacker Guide to Buying an ESP32 Camera Module That's Right for Your Project
 How To:
Perform Keystroke Injection Attacks Over Wi-Fi with Your Smartphone
How To:
Perform Keystroke Injection Attacks Over Wi-Fi with Your Smartphone
 How To:
Use RedRabbit for Pen-Testing & Post-Exploitation of Windows Machines
How To:
Use RedRabbit for Pen-Testing & Post-Exploitation of Windows Machines
 How To:
Hack Computers Over Wi-Fi with the WiFi Duck Payload Deliverer
How To:
Hack Computers Over Wi-Fi with the WiFi Duck Payload Deliverer
 How To:
Use Mitaka to Perform In-Browser OSINT to Identify Malware, Sketchy Sites, Shady Emails & More
How To:
Use Mitaka to Perform In-Browser OSINT to Identify Malware, Sketchy Sites, Shady Emails & More
 How To:
Code a Dead Man's Switch in Python 3 to Encrypt & Delete Files Whenever You Don't Check In
How To:
Code a Dead Man's Switch in Python 3 to Encrypt & Delete Files Whenever You Don't Check In
 How To:
Use a Directional Antenna with ESP8266-Based Microcontroller
How To:
Use a Directional Antenna with ESP8266-Based Microcontroller
 How To:
Create a USB Mouse Jiggler to Keep a Target Computer from Falling Asleep (& Prank Friends Too)
How To:
Create a USB Mouse Jiggler to Keep a Target Computer from Falling Asleep (& Prank Friends Too)
 How To:
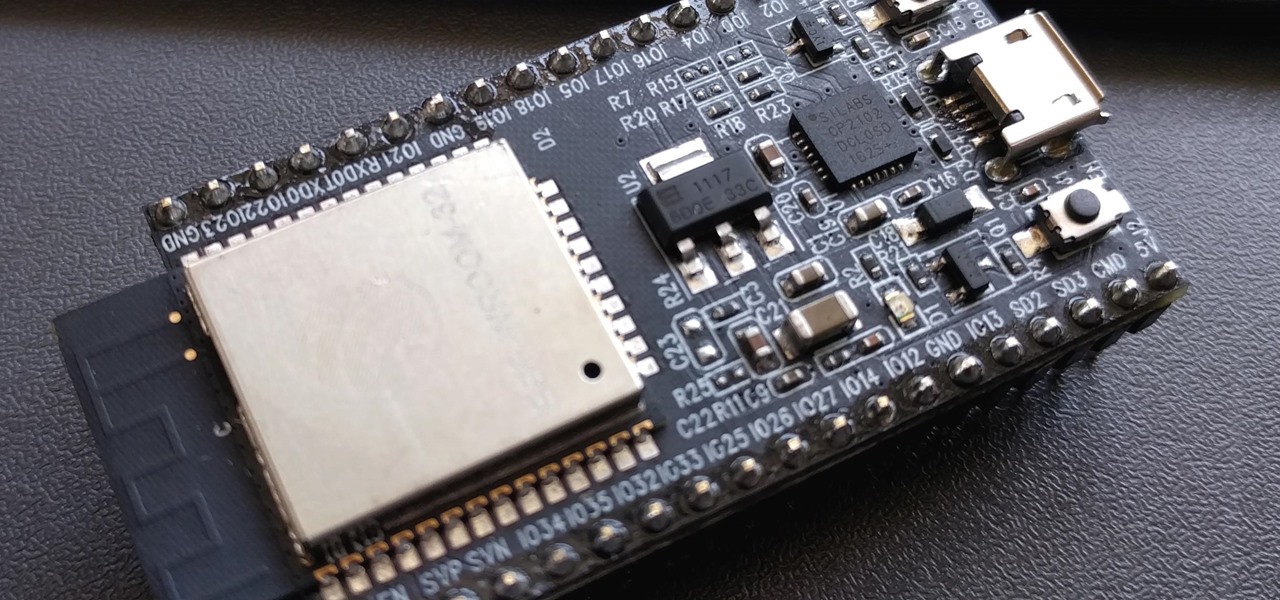
Program an ESP8266 or ESP32 Microcontroller Over Wi-Fi with MicroPython
How To:
Program an ESP8266 or ESP32 Microcontroller Over Wi-Fi with MicroPython
 How To:
Control Electronics from a Browser Using MicroPython in Jupyter Notebook
How To:
Control Electronics from a Browser Using MicroPython in Jupyter Notebook
 How To:
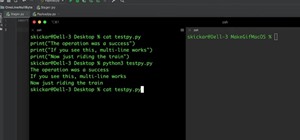
Execute Hidden Python Commands in a One-Line Stager
How To:
Execute Hidden Python Commands in a One-Line Stager
 How To:
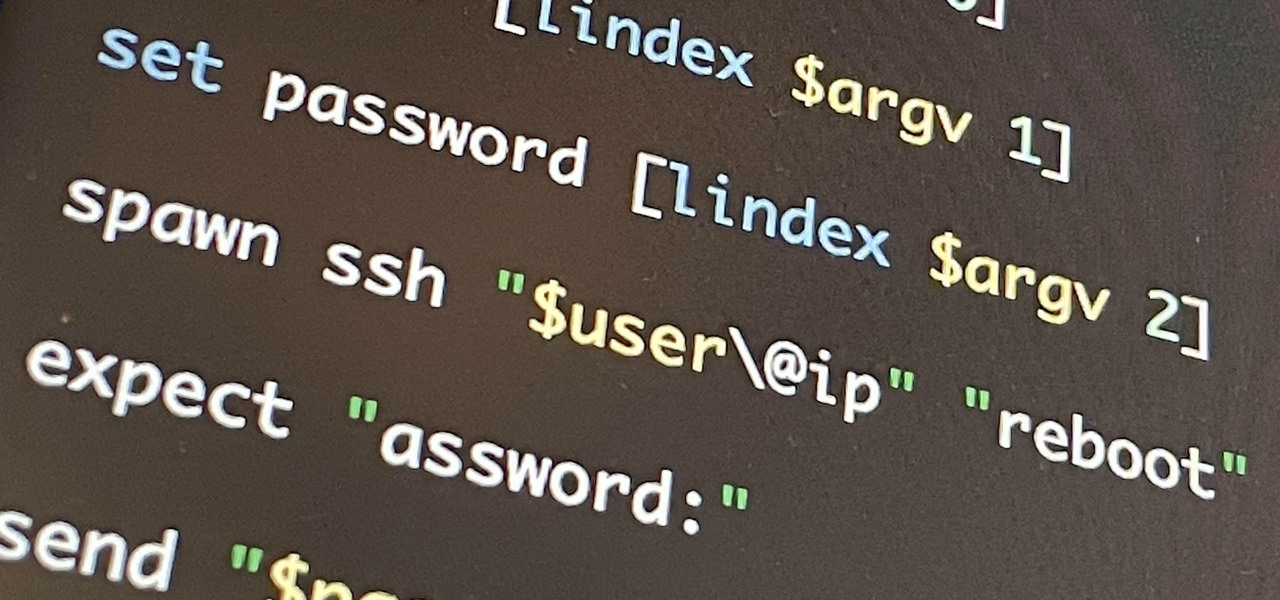
Automate Remote SSH Control of Computers with Expect Scripts
How To:
Automate Remote SSH Control of Computers with Expect Scripts
 How To:
Intercept & Analyze LAN Traffic with a Packet Squirrel & Wireshark
How To:
Intercept & Analyze LAN Traffic with a Packet Squirrel & Wireshark
 How To:
Enable Offline Chat Communications Over Wi-Fi with an ESP32
How To:
Enable Offline Chat Communications Over Wi-Fi with an ESP32
 How To:
Create Rogue APs with MicroPython on an ESP8266 Microcontroller
How To:
Create Rogue APs with MicroPython on an ESP8266 Microcontroller
 How To:
The Null Byte Guide to 3D Printing for Hackers
How To:
The Null Byte Guide to 3D Printing for Hackers
Next Page
Prev Page
Sites
- Hot
- Latest
-
 How To:
Make Spoofed Calls Using Any Phone Number You Want Right from Your Smartphone
How To:
Make Spoofed Calls Using Any Phone Number You Want Right from Your Smartphone
-
 How To:
Perform Advanced Man-in-the-Middle Attacks with Xerosploit
How To:
Perform Advanced Man-in-the-Middle Attacks with Xerosploit
-
 How To:
Unlock Facial Detection & Recognition on the Inexpensive ESP32-Based Wi-Fi Spy Camera
How To:
Unlock Facial Detection & Recognition on the Inexpensive ESP32-Based Wi-Fi Spy Camera
-
 How To:
Set Up a Wi-Fi Spy Camera with an ESP32-CAM
How To:
Set Up a Wi-Fi Spy Camera with an ESP32-CAM
-
 How To:
Hack Networks & Devices Right from Your Wrist with the Wi-Fi Deauther Watch
How To:
Hack Networks & Devices Right from Your Wrist with the Wi-Fi Deauther Watch
-
 How To:
Install Kali Linux as a Portable Live USB for Pen-Testing & Hacking on Any Computer
How To:
Install Kali Linux as a Portable Live USB for Pen-Testing & Hacking on Any Computer
-
 How To:
Play Wi-Fi Hacking Games Using Microcontrollers to Practice Wi-Fi Attacks Legally
How To:
Play Wi-Fi Hacking Games Using Microcontrollers to Practice Wi-Fi Attacks Legally
-
 How To:
Use a Directional Antenna with ESP8266-Based Microcontroller
How To:
Use a Directional Antenna with ESP8266-Based Microcontroller
-
 How To:
There Are Hidden Wi-Fi Networks All Around You — These Attacks Will Find Them
How To:
There Are Hidden Wi-Fi Networks All Around You — These Attacks Will Find Them
-
 How To:
Generate Crackable Wi-Fi Handshakes with an ESP8266-Based Test Network
How To:
Generate Crackable Wi-Fi Handshakes with an ESP8266-Based Test Network
-
 How To:
Automate Remote SSH Control of Computers with Expect Scripts
How To:
Automate Remote SSH Control of Computers with Expect Scripts
-
 How To:
Write Your Own Bash Scripts to Automate Tasks on Linux
How To:
Write Your Own Bash Scripts to Automate Tasks on Linux
-
 How To:
Create a USB Mouse Jiggler to Keep a Target Computer from Falling Asleep (& Prank Friends Too)
How To:
Create a USB Mouse Jiggler to Keep a Target Computer from Falling Asleep (& Prank Friends Too)
-
 How To:
Use RedRabbit for Pen-Testing & Post-Exploitation of Windows Machines
How To:
Use RedRabbit for Pen-Testing & Post-Exploitation of Windows Machines
-
 How To:
Null Byte's Hacker Guide to Buying an ESP32 Camera Module That's Right for Your Project
How To:
Null Byte's Hacker Guide to Buying an ESP32 Camera Module That's Right for Your Project
-
 How To:
Perform Keystroke Injection Attacks Over Wi-Fi with Your Smartphone
How To:
Perform Keystroke Injection Attacks Over Wi-Fi with Your Smartphone
-
 How To:
Get an Internet Connection in the Middle of Nowhere to Hack Remotely
How To:
Get an Internet Connection in the Middle of Nowhere to Hack Remotely
-
 How To:
Use Upip to Load MicroPython Libraries onto a Microcontroller Over Wi-Fi
How To:
Use Upip to Load MicroPython Libraries onto a Microcontroller Over Wi-Fi
-
 How To:
Extract Bitcoin Wallet Addresses & Balances from Websites with SpiderFoot CLI
How To:
Extract Bitcoin Wallet Addresses & Balances from Websites with SpiderFoot CLI
-
 How To:
Hack Computers Over Wi-Fi with the WiFi Duck Payload Deliverer
How To:
Hack Computers Over Wi-Fi with the WiFi Duck Payload Deliverer
-
 How To:
Make Spoofed Calls Using Any Phone Number You Want Right from Your Smartphone
How To:
Make Spoofed Calls Using Any Phone Number You Want Right from Your Smartphone
-
 How To:
Set Up a Wi-Fi Spy Camera with an ESP32-CAM
How To:
Set Up a Wi-Fi Spy Camera with an ESP32-CAM
-
 How To:
Use Upip to Load MicroPython Libraries onto a Microcontroller Over Wi-Fi
How To:
Use Upip to Load MicroPython Libraries onto a Microcontroller Over Wi-Fi
-
 How To:
Extract Bitcoin Wallet Addresses & Balances from Websites with SpiderFoot CLI
How To:
Extract Bitcoin Wallet Addresses & Balances from Websites with SpiderFoot CLI
-
 How To:
Perform Advanced Man-in-the-Middle Attacks with Xerosploit
How To:
Perform Advanced Man-in-the-Middle Attacks with Xerosploit
-
 How To:
There Are Hidden Wi-Fi Networks All Around You — These Attacks Will Find Them
How To:
There Are Hidden Wi-Fi Networks All Around You — These Attacks Will Find Them
-
 How To:
Conduct Wireless Recon on Bluetooth, Wi-Fi & GPS with Sparrow-wifi
How To:
Conduct Wireless Recon on Bluetooth, Wi-Fi & GPS with Sparrow-wifi
-
 How To:
Generate Crackable Wi-Fi Handshakes with an ESP8266-Based Test Network
How To:
Generate Crackable Wi-Fi Handshakes with an ESP8266-Based Test Network
-
 How To:
Install Kali Linux as a Portable Live USB for Pen-Testing & Hacking on Any Computer
How To:
Install Kali Linux as a Portable Live USB for Pen-Testing & Hacking on Any Computer
-
 How To:
Unlock Facial Detection & Recognition on the Inexpensive ESP32-Based Wi-Fi Spy Camera
How To:
Unlock Facial Detection & Recognition on the Inexpensive ESP32-Based Wi-Fi Spy Camera
-
 How To:
Analyze Web Browser Extensions for Possible Malware & Other Malicious Activity
How To:
Analyze Web Browser Extensions for Possible Malware & Other Malicious Activity
-
 How To:
Hack Networks & Devices Right from Your Wrist with the Wi-Fi Deauther Watch
How To:
Hack Networks & Devices Right from Your Wrist with the Wi-Fi Deauther Watch
-
 How To:
Write Your Own Bash Scripts to Automate Tasks on Linux
How To:
Write Your Own Bash Scripts to Automate Tasks on Linux
-
 How To:
Find OSINT Data on License Plate Numbers with Skiptracer
How To:
Find OSINT Data on License Plate Numbers with Skiptracer
-
 How To:
Play Wi-Fi Hacking Games Using Microcontrollers to Practice Wi-Fi Attacks Legally
How To:
Play Wi-Fi Hacking Games Using Microcontrollers to Practice Wi-Fi Attacks Legally
-
 How To:
Build an Off-Grid Wi-Fi Voice Communication System with Android & Raspberry Pi
How To:
Build an Off-Grid Wi-Fi Voice Communication System with Android & Raspberry Pi
-
 How To:
Get an Internet Connection in the Middle of Nowhere to Hack Remotely
How To:
Get an Internet Connection in the Middle of Nowhere to Hack Remotely
-
 How To:
Null Byte's Hacker Guide to Buying an ESP32 Camera Module That's Right for Your Project
How To:
Null Byte's Hacker Guide to Buying an ESP32 Camera Module That's Right for Your Project
-
 How To:
Perform Keystroke Injection Attacks Over Wi-Fi with Your Smartphone
How To:
Perform Keystroke Injection Attacks Over Wi-Fi with Your Smartphone
-
 How To:
Use RedRabbit for Pen-Testing & Post-Exploitation of Windows Machines
How To:
Use RedRabbit for Pen-Testing & Post-Exploitation of Windows Machines
-
 How To:
Hack Computers Over Wi-Fi with the WiFi Duck Payload Deliverer
How To:
Hack Computers Over Wi-Fi with the WiFi Duck Payload Deliverer
-
 How To:
Use Mitaka to Perform In-Browser OSINT to Identify Malware, Sketchy Sites, Shady Emails & More
How To:
Use Mitaka to Perform In-Browser OSINT to Identify Malware, Sketchy Sites, Shady Emails & More
-
 How To:
Code a Dead Man's Switch in Python 3 to Encrypt & Delete Files Whenever You Don't Check In
How To:
Code a Dead Man's Switch in Python 3 to Encrypt & Delete Files Whenever You Don't Check In
-
 How To:
Use a Directional Antenna with ESP8266-Based Microcontroller
How To:
Use a Directional Antenna with ESP8266-Based Microcontroller
-
 How To:
Create a USB Mouse Jiggler to Keep a Target Computer from Falling Asleep (& Prank Friends Too)
How To:
Create a USB Mouse Jiggler to Keep a Target Computer from Falling Asleep (& Prank Friends Too)
-
 How To:
Program an ESP8266 or ESP32 Microcontroller Over Wi-Fi with MicroPython
How To:
Program an ESP8266 or ESP32 Microcontroller Over Wi-Fi with MicroPython
-
 How To:
Control Electronics from a Browser Using MicroPython in Jupyter Notebook
How To:
Control Electronics from a Browser Using MicroPython in Jupyter Notebook
-
 How To:
Execute Hidden Python Commands in a One-Line Stager
How To:
Execute Hidden Python Commands in a One-Line Stager
-
 How To:
Automate Remote SSH Control of Computers with Expect Scripts
How To:
Automate Remote SSH Control of Computers with Expect Scripts
-
 How To:
Intercept & Analyze LAN Traffic with a Packet Squirrel & Wireshark
How To:
Intercept & Analyze LAN Traffic with a Packet Squirrel & Wireshark
-
 How To:
Enable Offline Chat Communications Over Wi-Fi with an ESP32
How To:
Enable Offline Chat Communications Over Wi-Fi with an ESP32
-
 How To:
Create Rogue APs with MicroPython on an ESP8266 Microcontroller
How To:
Create Rogue APs with MicroPython on an ESP8266 Microcontroller
-
 How To:
The Null Byte Guide to 3D Printing for Hackers
How To:
The Null Byte Guide to 3D Printing for Hackers