About Jack Sea
"The darker it gets, the brighter his blade shines."
Jack Sea's Popular Posts
Forum Thread : What Is the Latest Null Byte News?
It's been 6 months since I have checked in the site and a lot has already changed. While I like the sleek new design, it seems more suitable for a mobile device than a desktop. I've also heard WHT secured a new security author, which is nice. Have any veterans returned? Any n ...more
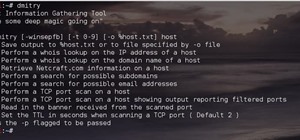
 How To:
Use Dmitry Effectively.
How To:
Use Dmitry Effectively.
Forum Thread : Quick Poll
Which of the following should I focus on? A 5-6 part series teaching IT hardware fundamentals A 5-6 part series teaching Python libraries Resuming my series on Banks Creating and Managing databases using SQL I've been hitting a brick wall with my current project (Breaking th ...more
Forum Thread : Until WHT Hires a New Admin.
A few things. Please stop complaining about how the 'community is dead'. There are a few things you can do if you really want to keep this place alive until they find a replacement: Share news articles and hold interesting discussions, but make sure to properly cite sources ...more
Forum Thread : How to Destroy Kali
This is pretty much a troll post. I was playing around in Kali light and decided to have some fun with the rm command. Obviously you should NEVER do this, but the command is rm -r with the star operator. After 20 seconds, my VM has become lifeless. A great prank if you have a ...more
Forum Thread : Decisions, Decisions.
I'm sure most of you are aware of the recent incident that has happened regarding OTW and his leave of Null Byte. Many users have voiced that they are going to leave the community, and OTW already scoffed on twitter that NB is now dead. 12 hours ago OTW posted on twitter tha ...more
Forum Thread : Breaking the Bank
Heyyy mates. I've been really procrastinating lately, like..major procrastination. Getting to the point, I could use some help finishing Article 1 of a series that I briefly mentioned last December. Message me and I'll show you the article and you could maybe provide me with ...more
Forum Thread : Just Stumbled Upon a Frightening Article
http://null-byte.wonderhowto.com/how-to/create-bump-key-open-any-door-0130500/ An important aspect of being a white hat, is also knowing about physical security, but this is just scary at how easily it is to breach a locked door. This is probably the reason we have biometric ...more
Forum Thread : White Hat Ethics
Greetings security enthusiasts, for the longest time I have been pondering what I could write about. While most of you know how to act, some of the newcomers could use a few pointers. First off, Null Byte is a white hat environment. We bring up security issues, discussing pur ...more
Forum Thread : Hydra Custom Pw List
As the title suggests, I'm going to make a custom pw list for Hydra (which I am just now learning..about time) I have the following Python script below as a test for having 4 letter passwords (Just a quick proof of concept) #Import libraries import random import string #Ini ...more
Forum Thread : An Apple a day keeps big brother away.
With the recent conflict between Apple and the FBI, the integrity of all data is being put at risk. By all data, I am referring to iPhone users alone. If someone truly wishes to be anonymous, they wouldn't use an iPhone in the first place. The industry is already struggling t ...more
Forum Thread : Best CCIE Resources?
In a month I'll be competing in a cybersecurity event for FBLA's yearly state conference, and a majority of the study material they posted comes from the CCIE or Security+. I'm going to be making flash cards and such, but having an actual study guide would be nice.
Forum Thread : 25/1/2016 Updates
Greeting my fellow security enthusiasts! It was just a few weeks ago when I announced my plans for a new series (due to the request of numerous script kiddies), but there are just so many things to write about and so little time to actually work on these tutorials. Breaking t ...more
Forum Thread : Just Found an Amazing Intel-Gathering Tool
It's called Email Hunter. The chrome extension searches a website for emails, which is pretty useful. Just another tool in the ever-so-growing arsenal that we have here. There was a post a while back on another intel gathering engine called "Censys" which I also recommend ta ...more
Forum Thread : Active White-Hat Forums?
I've been digging around and found dozens of forums related to pentesting, hacking, etc but a majority of them are inactive, have few posts, or the last post was like 2 years ago. I haven't checked the onion yet, but I figure there must be some more forums on there that are a ...more
 News:
Predictions for the New Year
News:
Predictions for the New Year
Forum Thread : [2016] Let's Get It Over With.
The only thing I have to my name is a really short tut on hacking wordpress which is more like a methodology since I really provide no actual hacking commands or tools to use. I'm going to try to produce some quality posts this year and have a few ideas in mind: Tales from t ...more
Forum Thread : Negativity on the Forums
I made this same post like 5 months ago, but it is still pretty relevant. While there are some bad posts on the forum, I see a majority of posts being downvoted or given negative kudos. Seeing as how all the recent ones are "-1" with 0 comments, it looks like someone just scr ...more
Forum Thread : The Media Is Hyping Up ISIS "Hackers"
http://www.msn.com/en-us/news/technology/are-isis-hackers-trying-to-destroy-the-internet/ar-BBnEEQy?li=BBnb7Kz Last I checked, they are incompetent script kiddies and nothing more.
Forum Thread : A small thing I noticed
I can type in "Python" and find like half a dozen beginner tutorials about how to print and assign variables, but little beyond the beginner lessons. Would it be useful if I wanted to add on to these existing tutorials or should I do something else?
Forum Thread : For Any of You Apple Users Out There
Once again, Phishing takes the main stage of cybersecurity. What are your thoughts on this newest scam? CyberheistNews Vol #5 #52 Scam Of The Week: Apple ID Suspension Phish With A Twist. CyberheistNews Vol #5 #52 Scam Of The Week: Apple ID Suspension Phish With A Twist
Forum Thread : New Kali Linux
Ok ok I wasn't concise, but Kali Linux (2.0?) came out and I was wondering if everything is the same with it (besides the looks.) I've been digging around in it since I bought a course on pentesting, so hopefully nothing too severe has changed.
Forum Thread : Ayyyyyy I'm Back
Greetings greenhorn hackers, I am Jack Sea, aka the guy who's really done nothing here but make a semi-decent wordpress hack discussion and maybe make a few good replies regarding cybersecurity. I've seen a few amazing posts when I've checked in periodically and hope that one ...more
Forum Thread : WordPress Hackage [2]
Since my chromebook apparently cannot post replies, I'm making a new thread to talk about wordpress hacking (not in depth tutorial, just the basic steps) Obviously the first task is to locate your site. For example, let's say www.jacksnotwordpress.com Some high quality busin ...more
Forum Thread : What's with the Negative Kudos Spree?
A majority of posts I see on here usually had positive kudos, but recently a ton of posts are being down voted, even ones that are useful or are just asking questions. Heck, someone's "introduction" was downvoted...such a warm welcome. I know a few were downvoted for a legit ...more
Forum Thread : Best Way to Deal with Script Kiddies?
Since most of them are under the age of 18 and live in the US (well, the ones I deal with at least) I doubt any real authorities would bother with them. The most effective method I can think of is finding their information and emailing their parents or a local official. What ...more
Forum Thread : Pretty Amusing Phishing Story
You know how college students are always in debt right? Well one decided that they wanted to get through college with free tuition. This person (not naming gender or any other identifiers) looked up the basics of phishing and managed to send fake emails to fellow students, te ...more
Forum Thread : Adware Attack ;-;
This isn't some "help me im hacked!!!" post, but just a general note about the ever so growing adware problem. For so long I have ignored ad blockers, anti-spyware programs, and other useful software simply because I never had adware. Until today..logging in I discover page a ...more
Forum Thread : Hacking with Windows (Hypothetical)
I saw a recent post asking how to hack with windows, to which (no surprise) people instead recommended using kali. I'll admit, Windows is not the optical hacking system, mainly because it was not even designed for that. However, in my current position irl, I cannot exactly shr ...more
Forum Thread : Null Byte Articles on Fixing Vulnerabilities?
Before anyone comments some snide remark like, "There's a search bar for a reason", I have checked Null Byte for anything pertaining to fixing vulnerabilities. However everything I find seems to be about creating these exploits or exploiting them. I understand the importance ...more
Forum Thread : Best Linux Video Tutorials?
This forum has a lot of useful guides on Linux basics, but I am terrible at learning just by reading. I need to see or actually do something in order to learn it. I tried looking around youtube but a majority of ones I found are either incomplete or focused on specific hack to ...more
Forum Thread : Computer Science Puns
Sorry for any interruption, but I've been working on puns pertaining to "buffer overflow(s)" but it's almost as though my memory was wiped because I am unable to think of any. Post any security puns below so I can use them in IT class tomorrow.
Forum Thread : Lack of Originality in Digital Photography
This is not a "how-to" but a simple post regarding a lack of creativity in a lot of graphic design recently. I want to see if anyone else has similair thoughts. Recently my school had a "photography" show to show off...well...photos. The photoshop section was terrible and the ...more
- Hot
- Latest
-
 Forum Thread:
What Is the Latest Null Byte News?
0
Replies
Forum Thread:
What Is the Latest Null Byte News?
0
Replies
7 yrs ago -
 How To:
Use Dmitry Effectively.
How To:
Use Dmitry Effectively.
-
 Forum Thread:
Quick Poll
3
Replies
Forum Thread:
Quick Poll
3
Replies
7 yrs ago -
 Forum Thread:
Until WHT Hires a New Admin.
3
Replies
Forum Thread:
Until WHT Hires a New Admin.
3
Replies
7 yrs ago -
 Forum Thread:
How to Destroy Kali
4
Replies
Forum Thread:
How to Destroy Kali
4
Replies
7 yrs ago -
 Forum Thread:
Decisions, Decisions.
2
Replies
Forum Thread:
Decisions, Decisions.
2
Replies
7 yrs ago -
 Forum Thread:
Breaking the Bank
3
Replies
Forum Thread:
Breaking the Bank
3
Replies
8 yrs ago -
 Forum Thread:
Just Stumbled Upon a Frightening Article
0
Replies
Forum Thread:
Just Stumbled Upon a Frightening Article
0
Replies
8 yrs ago -
 Forum Thread:
White Hat Ethics
3
Replies
Forum Thread:
White Hat Ethics
3
Replies
8 yrs ago -
 Forum Thread:
Hydra Custom Pw List
4
Replies
Forum Thread:
Hydra Custom Pw List
4
Replies
8 yrs ago -
 Forum Thread:
An Apple a day keeps big brother away.
0
Replies
Forum Thread:
An Apple a day keeps big brother away.
0
Replies
8 yrs ago -
 Forum Thread:
Best CCIE Resources?
0
Replies
Forum Thread:
Best CCIE Resources?
0
Replies
8 yrs ago -
How To: Bypassing School Security (White-Hat)
-
 Forum Thread:
25/1/2016 Updates
7
Replies
Forum Thread:
25/1/2016 Updates
7
Replies
8 yrs ago -
 Forum Thread:
Just Found an Amazing Intel-Gathering Tool
1
Replies
Forum Thread:
Just Found an Amazing Intel-Gathering Tool
1
Replies
8 yrs ago -
 Forum Thread:
Active White-Hat Forums?
13
Replies
Forum Thread:
Active White-Hat Forums?
13
Replies
8 yrs ago -
 News:
Predictions for the New Year
News:
Predictions for the New Year
-
 Forum Thread:
[2016] Let's Get It Over With.
2
Replies
Forum Thread:
[2016] Let's Get It Over With.
2
Replies
8 yrs ago -
 Forum Thread:
Negativity on the Forums
3
Replies
Forum Thread:
Negativity on the Forums
3
Replies
8 yrs ago -
 Forum Thread:
The Media Is Hyping Up ISIS "Hackers"
4
Replies
Forum Thread:
The Media Is Hyping Up ISIS "Hackers"
4
Replies
8 yrs ago
-
How To: Bypassing School Security (White-Hat)
-
 Forum Thread:
What Is the Latest Null Byte News?
0
Replies
Forum Thread:
What Is the Latest Null Byte News?
0
Replies
7 yrs ago -
 How To:
Use Dmitry Effectively.
How To:
Use Dmitry Effectively.
-
 Forum Thread:
Quick Poll
3
Replies
Forum Thread:
Quick Poll
3
Replies
7 yrs ago -
 Forum Thread:
Until WHT Hires a New Admin.
3
Replies
Forum Thread:
Until WHT Hires a New Admin.
3
Replies
7 yrs ago -
 Forum Thread:
How to Destroy Kali
4
Replies
Forum Thread:
How to Destroy Kali
4
Replies
7 yrs ago -
 Forum Thread:
Decisions, Decisions.
2
Replies
Forum Thread:
Decisions, Decisions.
2
Replies
7 yrs ago -
 Forum Thread:
Breaking the Bank
3
Replies
Forum Thread:
Breaking the Bank
3
Replies
8 yrs ago -
 Forum Thread:
Just Stumbled Upon a Frightening Article
0
Replies
Forum Thread:
Just Stumbled Upon a Frightening Article
0
Replies
8 yrs ago -
 Forum Thread:
White Hat Ethics
3
Replies
Forum Thread:
White Hat Ethics
3
Replies
8 yrs ago -
 Forum Thread:
Hydra Custom Pw List
4
Replies
Forum Thread:
Hydra Custom Pw List
4
Replies
8 yrs ago -
 Forum Thread:
An Apple a day keeps big brother away.
0
Replies
Forum Thread:
An Apple a day keeps big brother away.
0
Replies
8 yrs ago -
 Forum Thread:
Best CCIE Resources?
0
Replies
Forum Thread:
Best CCIE Resources?
0
Replies
8 yrs ago -
 Forum Thread:
25/1/2016 Updates
7
Replies
Forum Thread:
25/1/2016 Updates
7
Replies
8 yrs ago -
 Forum Thread:
Just Found an Amazing Intel-Gathering Tool
1
Replies
Forum Thread:
Just Found an Amazing Intel-Gathering Tool
1
Replies
8 yrs ago -
 Forum Thread:
Active White-Hat Forums?
13
Replies
Forum Thread:
Active White-Hat Forums?
13
Replies
8 yrs ago -
 News:
Predictions for the New Year
News:
Predictions for the New Year
-
 Forum Thread:
[2016] Let's Get It Over With.
2
Replies
Forum Thread:
[2016] Let's Get It Over With.
2
Replies
8 yrs ago -
 Forum Thread:
Negativity on the Forums
3
Replies
Forum Thread:
Negativity on the Forums
3
Replies
8 yrs ago -
 Forum Thread:
The Media Is Hyping Up ISIS "Hackers"
4
Replies
Forum Thread:
The Media Is Hyping Up ISIS "Hackers"
4
Replies
8 yrs ago -
 Forum Thread:
A small thing I noticed
4
Replies
Forum Thread:
A small thing I noticed
4
Replies
8 yrs ago -
 Forum Thread:
For Any of You Apple Users Out There
0
Replies
Forum Thread:
For Any of You Apple Users Out There
0
Replies
8 yrs ago -
 Forum Thread:
New Kali Linux
1
Replies
Forum Thread:
New Kali Linux
1
Replies
8 yrs ago -
 Forum Thread:
Ayyyyyy I'm Back
4
Replies
Forum Thread:
Ayyyyyy I'm Back
4
Replies
8 yrs ago -
 Forum Thread:
WordPress Hackage [2]
11
Replies
Forum Thread:
WordPress Hackage [2]
11
Replies
8 yrs ago -
 Forum Thread:
What's with the Negative Kudos Spree?
21
Replies
Forum Thread:
What's with the Negative Kudos Spree?
21
Replies
8 yrs ago -
 Forum Thread:
Best Way to Deal with Script Kiddies?
16
Replies
Forum Thread:
Best Way to Deal with Script Kiddies?
16
Replies
8 yrs ago -
 Forum Thread:
Pretty Amusing Phishing Story
3
Replies
Forum Thread:
Pretty Amusing Phishing Story
3
Replies
8 yrs ago -
 Forum Thread:
Adware Attack ;-;
5
Replies
Forum Thread:
Adware Attack ;-;
5
Replies
8 yrs ago -
 Forum Thread:
Hacking with Windows (Hypothetical)
9
Replies
Forum Thread:
Hacking with Windows (Hypothetical)
9
Replies
8 yrs ago -
 Forum Thread:
Null Byte Articles on Fixing Vulnerabilities?
11
Replies
Forum Thread:
Null Byte Articles on Fixing Vulnerabilities?
11
Replies
8 yrs ago -
 Forum Thread:
Best Linux Video Tutorials?
1
Replies
Forum Thread:
Best Linux Video Tutorials?
1
Replies
8 yrs ago -
 Forum Thread:
Computer Science Puns
2
Replies
Forum Thread:
Computer Science Puns
2
Replies
8 yrs ago -
 Forum Thread:
Lack of Originality in Digital Photography
1
Replies
Forum Thread:
Lack of Originality in Digital Photography
1
Replies
8 yrs ago



