About Alex Long
Hi, I'm Alex. I'm a young computer and tech enthusiast, focused on bringing the best of tech news and hacking to the table. I'll teach anyone who's willing to learn all that I know .about tech.
- Location: USA
- Website: twitter.com
Alex Long's Latest Posts
News: Advanced Cracking Techniques, Part 2: Intelligent Bruteforcing
News: Advanced Cracking Techniques, Part 1: Custom Dictionaries
How To: Unban Your Xbox LIVE Account That is Banned Until 12/31/9999 by Tricking Microsoft's Banning System
How To: The Penny Pinchers Guide to Eating Cost Effectively Without Relying on Ramen
How To: How Anyone Can Retire Early & Wealthy, Part 2: Tax Liens
News: Flaw in Facebook & Google Allows Phishing, Spam & More
News : Beware Angry Birds Malware
How To: How Anyone Can Retire Early & Wealthy, Part 1: CDs
Community Byte: HackThisSite, Realistic 1 - Real Hacking Simulations
News : Call to Webmasters Everywhere
Goodnight Byte: HackThisSite Walkthrough, Part 10 - Legal Hacker Training
How To: Spider Web Pages with Nmap for SQLi Vulnerabilities
Weekend Homework: How to Become a Null Byte Contributor
 How To:
Hack Your Kindle Touch to Get It Ready for Homebrew Apps & More
How To:
Hack Your Kindle Touch to Get It Ready for Homebrew Apps & More
 How To:
Add Your Own Custom Screensaver Images to Your Kindle Lock Screen
How To:
Add Your Own Custom Screensaver Images to Your Kindle Lock Screen
How To: Build Your Own "Pogo Mo Thoin" to Flash Any Xbox 360 DVD Drive for Under $5
How To: Make Your Own USB Keylogger Hardware
How To: Create a Reverse Shell to Remotely Execute Root Commands Over Any Open Port Using NetCat or BASH
How To: Remotely Control Computers Over VNC Securely with SSH
Community Byte: HackThisSite Walkthrough, Part 10 - Legal Hacker Training
Goodnight Byte: HackThisSite Walkthrough, Part 9 - Legal Hacker Training
UDP Flooding: How to Kick a Local User Off the Network
How To: The Hacks Behind Cracking, Part 2: How to Generate Software Keys
How To: The Hacks Behind Cracking, Part 1: How to Bypass Software Registration
News: Null Byte Is Calling for Contributors!
How To: Get Your AMD Graphics, Sound & Other Drivers to Work in Linux on Your Laptop
 How To:
Hack WPA WiFi Passwords by Cracking the WPS PIN
How To:
Hack WPA WiFi Passwords by Cracking the WPS PIN
How To: Run a Free Web Server From Home on Windows or Linux with Apache
How To: Turn Your House Lights On & Off Using the Internet
Community Byte: HackThisSite Walkthrough, Part 9 - Legal Hacker Training
Goodnight Byte: HackThisSite Walkthrough, Part 8 - Legal Hacker Training
How To: Get Free Netflix for Life
How To: Hack a Radio to Pick Up Different Frequencies - Including Law Enforcement & More
How To: Hack Coin-Operated Laudromat Machines for Free Wash & Dry Cycles
News: Flaw in Wal-Mart Returns System Allows Major Thefts to Go Unnoticed
How To: Social Engineer Your Debt Collectors Into Giving You More Time to Pay Bills
Community Byte: HackThisSite Walkthrough, Part 8 - Legal Hacker Training
Goodnight Byte: HackThisSite Walkthrough, Part 7 - Legal Hacker
How To: Your Guide to Buying Computer Parts: How to Get the Most for Your Money
- Hot
- Latest
-
 Farewell Byte:
Goodbye Alex, Welcome Allen
Farewell Byte:
Goodbye Alex, Welcome Allen
-
 Goodnight Byte:
HackThisSite, Realistic 5 - Real Hacking Simulations
Goodnight Byte:
HackThisSite, Realistic 5 - Real Hacking Simulations
-
 Advanced Social Engineering:
The Mind Hacks Behind Brainwashing
Advanced Social Engineering:
The Mind Hacks Behind Brainwashing
-
 News:
Fend Off Attackers Using This Scary Hot DIY Pepper Spray
News:
Fend Off Attackers Using This Scary Hot DIY Pepper Spray
-
 Weekend Homework:
How to Become a Null Byte Contributor (2/17/2012)
Weekend Homework:
How to Become a Null Byte Contributor (2/17/2012)
-
 Listen In:
Live Social Engineering Phone Calls with Professional Social Engineers (Final Session)
Listen In:
Live Social Engineering Phone Calls with Professional Social Engineers (Final Session)
-
 How To:
Safely Log In to Your SSH Account Without a Password
How To:
Safely Log In to Your SSH Account Without a Password
-
 Know Your Rights:
How to Escape Unlawful Stops and Police Searches with Social Engineering
Know Your Rights:
How to Escape Unlawful Stops and Police Searches with Social Engineering
-
 Xbox LIVE Achievement:
How to Earn Free Microsoft Points with Social Engineering
Xbox LIVE Achievement:
How to Earn Free Microsoft Points with Social Engineering
-
 Community Byte:
HackThisSite, Realistic 5 - Real Hacking Simulations
Community Byte:
HackThisSite, Realistic 5 - Real Hacking Simulations
-
 Goodnight Byte:
HackThisSite, Realistic 4 - Real Hacking Simulations
Goodnight Byte:
HackThisSite, Realistic 4 - Real Hacking Simulations
-
 Weekend Homework:
How to Become a Null Byte Contributor (2/10/2012)
Weekend Homework:
How to Become a Null Byte Contributor (2/10/2012)
-
 Listen In:
Live Social Engineering Phone Calls with Professional Social Engineers (Week 2)
Listen In:
Live Social Engineering Phone Calls with Professional Social Engineers (Week 2)
-
 News:
Catch Creeps and Thieves in Action: Set Up a Motion-Activated Webcam DVR in Linux
News:
Catch Creeps and Thieves in Action: Set Up a Motion-Activated Webcam DVR in Linux
-
 How To:
Dropped Your Phone in Water? The Quick Response Guide to Saving Wet Electronics
How To:
Dropped Your Phone in Water? The Quick Response Guide to Saving Wet Electronics
-
 How To:
Sneak Past Web Filters and Proxy Blockers with Google Translate
How To:
Sneak Past Web Filters and Proxy Blockers with Google Translate
-
 Community Contest:
Code the Best Hacking Tool, Win Bragging Rights
Community Contest:
Code the Best Hacking Tool, Win Bragging Rights
-
 How To:
Score Free Game Product Keys with Social Engineering
How To:
Score Free Game Product Keys with Social Engineering
-
 News:
Awesome Trick with Prepaid "GoPhones" Nabs You Free Text Messaging for Life
News:
Awesome Trick with Prepaid "GoPhones" Nabs You Free Text Messaging for Life
-
 Community Byte:
HackThisSite, Realistic 4 - Real Hacking Simulations
Community Byte:
HackThisSite, Realistic 4 - Real Hacking Simulations
-
 How To:
Hack Coin-Operated Laudromat Machines for Free Wash & Dry Cycles
How To:
Hack Coin-Operated Laudromat Machines for Free Wash & Dry Cycles
-
 How to Hack Your Game Saves:
A Basic Guide to Hex Editing
How to Hack Your Game Saves:
A Basic Guide to Hex Editing
-
 How Null Byte Injections Work:
A History of Our Namesake
How Null Byte Injections Work:
A History of Our Namesake
-
 How To:
The Hacks Behind Cracking, Part 1: How to Bypass Software Registration
How To:
The Hacks Behind Cracking, Part 1: How to Bypass Software Registration
-
 How To:
Fix Your Overheating, RRoD, or E74 Xbox 360 with Mere Pennies
How To:
Fix Your Overheating, RRoD, or E74 Xbox 360 with Mere Pennies
-
 How To:
Create a Reverse Shell to Remotely Execute Root Commands Over Any Open Port Using NetCat or BASH
How To:
Create a Reverse Shell to Remotely Execute Root Commands Over Any Open Port Using NetCat or BASH
-
 Rainbow Tables:
How to Create & Use Them to Crack Passwords
Rainbow Tables:
How to Create & Use Them to Crack Passwords
-
 How To:
How Hackers Use Your IP Address to Hack Your Computer & How to Stop It
How To:
How Hackers Use Your IP Address to Hack Your Computer & How to Stop It
-
 Social Engineering, Part 2:
Hacking a Friend's Facebook Password
Social Engineering, Part 2:
Hacking a Friend's Facebook Password
-
 How To:
Spy on the Web Traffic for Any Computers on Your Network: An Intro to ARP Poisoning
How To:
Spy on the Web Traffic for Any Computers on Your Network: An Intro to ARP Poisoning
-
 How To:
Hack WPA WiFi Passwords by Cracking the WPS PIN
How To:
Hack WPA WiFi Passwords by Cracking the WPS PIN
-
 How To:
Create a Bump Key to Open Any Door
How To:
Create a Bump Key to Open Any Door
-
 How To:
Hack Wireless Router Passwords & Networks Using Hydra
How To:
Hack Wireless Router Passwords & Networks Using Hydra
-
 How To:
Fix Defective Pixels & Improve Image Quality on LCD & LED Monitors
How To:
Fix Defective Pixels & Improve Image Quality on LCD & LED Monitors
-
 Remove Your Online Identity:
The Ultimate Guide to Anonymity and Security on the Internet
Remove Your Online Identity:
The Ultimate Guide to Anonymity and Security on the Internet
-
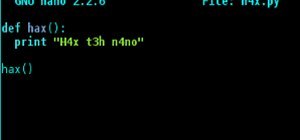
 How To:
Enable Code Syntax Highlighting for Python in the Nano Text Editor
How To:
Enable Code Syntax Highlighting for Python in the Nano Text Editor
-
 How To:
The Hacks Behind Cracking, Part 2: How to Generate Software Keys
How To:
The Hacks Behind Cracking, Part 2: How to Generate Software Keys
-
 How To:
A Guide to Steganography, Part 1: How to Hide Secret Messages in Images
How To:
A Guide to Steganography, Part 1: How to Hide Secret Messages in Images
-
 How To:
Get Packet Injection Capable Drivers in Linux
How To:
Get Packet Injection Capable Drivers in Linux
-
 How To:
Conceal a USB Flash Drive in Everyday Items
How To:
Conceal a USB Flash Drive in Everyday Items
-
 Goodnight Byte:
HackThisSite, Realistic 1 - Real Hacking Simulations
Goodnight Byte:
HackThisSite, Realistic 1 - Real Hacking Simulations
-
 How To:
Run an FTP Server from Home with Linux
How To:
Run an FTP Server from Home with Linux
-
 How To:
Use JavaScript Injections to Locally Manipulate the Websites You Visit
How To:
Use JavaScript Injections to Locally Manipulate the Websites You Visit
-
 News:
12 Easy Exploits to Raise Thief Skills in Skyrim
News:
12 Easy Exploits to Raise Thief Skills in Skyrim
-
 How To:
Reveal Saved Browser Passwords with JavaScript Injections
How To:
Reveal Saved Browser Passwords with JavaScript Injections
-
 How To:
How Hackers Steal Your Internet & How to Defend Against It
How To:
How Hackers Steal Your Internet & How to Defend Against It
-
 How To:
Hack a Radio to Pick Up Different Frequencies - Including Law Enforcement & More
How To:
Hack a Radio to Pick Up Different Frequencies - Including Law Enforcement & More
-
 How To:
GPU Accelerate Cracking Passwords with Hashcat
How To:
GPU Accelerate Cracking Passwords with Hashcat
-
 How To:
Burn an XDG3 Formatted Xbox 360 Game ISO with Windows
How To:
Burn an XDG3 Formatted Xbox 360 Game ISO with Windows
-
 How To:
Chain Proxies to Mask Your IP Address and Remain Anonymous on the Web
How To:
Chain Proxies to Mask Your IP Address and Remain Anonymous on the Web
-
 How To:
How Credit Card Algorithms Work: The Anatomy of Credit Card Numbers
How To:
How Credit Card Algorithms Work: The Anatomy of Credit Card Numbers
-
 How To:
Customize Your Linux Desktop
How To:
Customize Your Linux Desktop
-
 How To:
Create a Custom Arch Linux Distro
How To:
Create a Custom Arch Linux Distro
-
 News:
Hack Your Computer's BIOS to Unlock Hidden Settings, Overclocking & More
News:
Hack Your Computer's BIOS to Unlock Hidden Settings, Overclocking & More
-
 How To:
Nab Free eBooks Using Google
How To:
Nab Free eBooks Using Google
-
 UDP Flooding:
How to Kick a Local User Off the Network
UDP Flooding:
How to Kick a Local User Off the Network
-
 How To:
Fix a Bricked iPhone or iPod Touch After a Failed Jailbreak
How To:
Fix a Bricked iPhone or iPod Touch After a Failed Jailbreak
-
 Goodnight Byte:
HackThisSite, Realistic 4 - Real Hacking Simulations
Goodnight Byte:
HackThisSite, Realistic 4 - Real Hacking Simulations
-
 How To:
Unlock Padlocks Without a Key Using Cheap DIY Shims
How To:
Unlock Padlocks Without a Key Using Cheap DIY Shims
-
 How To:
Make the World's Hottest Burning Man-Made Substance: Thermite
How To:
Make the World's Hottest Burning Man-Made Substance: Thermite