Hot Posts

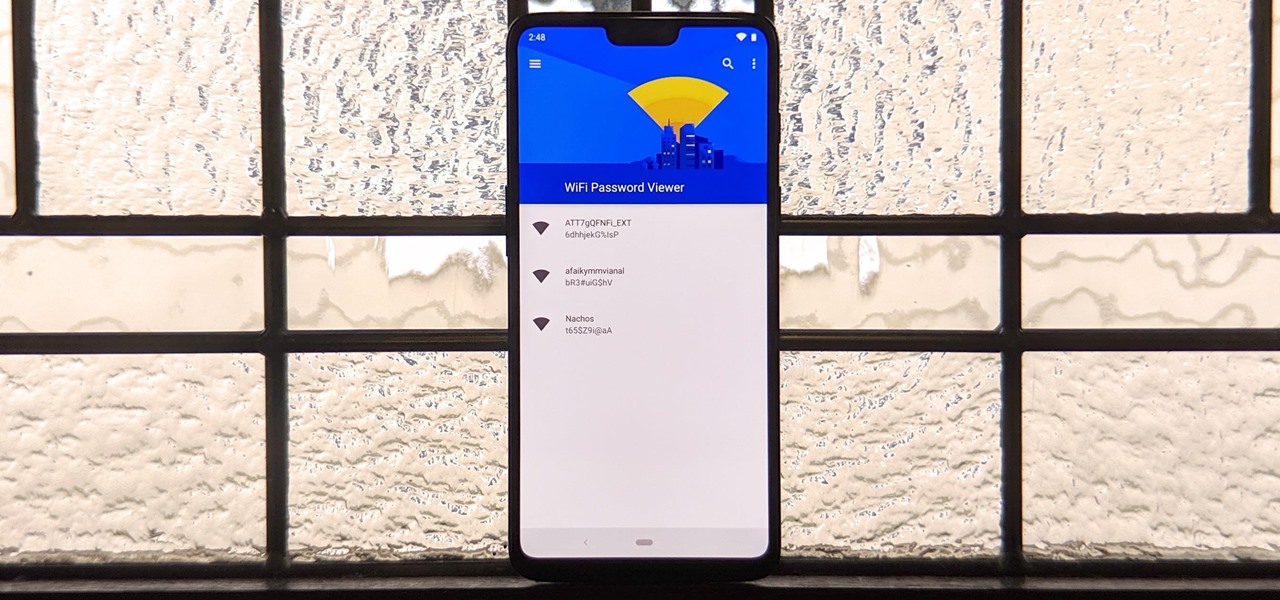
How To: See Passwords for Wi-Fi Networks You've Connected Your Android Device To
You've probably connected your Android device to dozens of Wi-Fi networks since you've had it, and your phone or tablet remembers each of them. Whether it's a hotspot at home, school, work, the gym, a coffee shop, a relative's apartment — or even from a friend's phone — each time you type in a Wi-Fi password, your Android device saves it for safekeeping and easy access later.

How To: The Messaging Trick You Never Knew You Needed
Whether you're wielding an iPhone, iPad, Mac, Android phone or tablet, or even a Windows PC, this little-known secret holds the key to effortless assistance and unwavering obedience. Intrigued? I thought so.

How To: Brute-Force Nearly Any Website Login with Hatch
The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.
How To: Install TWRP Recovery on Your Pixel 3a
TWRP is a name many are familiar with since it allows your Android device to install any custom file of your choosing. You can create a NANDroid backup to keep your data safe or even use Magisk to achieve full root access. In fact, TWRP is often seen as the gateway to modding your system for creating a unique user experience.

How To: Use FaceTime's Secret Hand Gestures and Reaction Buttons to Add Animated On-Screen Effects to Your Video Feed
Apple's Messages app has long had visual effects you could apply manually after long-pressing the send button, and there are even hidden keywords you could use to trigger full-screen effects automatically. FaceTime's latest update also gives you some full-screen effects to play around with during video calls, but the triggers are an entirely different concept — hand gestures.

How To: Dox Anyone
Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...

How To: Crack SSH Private Key Passwords with John the Ripper
Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

How To: Scan for Vulnerabilities on Any Website Using Nikto
Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

How To: Make Siri Say Whatever You Want Every Time You Connect Your iPhone to a Charger
Whenever your iPhone's ringer is on, you'll hear Apple's iconic "Connect Power" chime every time you connect it to a wired or wireless power source, which lets you know that charging has started. There's no way to disable the sound without turning on Silent mode, but there is a way to make Siri automatically say whatever you want after a successful connection.

How To: Make a Self-Freezing Coca-Cola Slushy (Or Any Kind of Instant Soda Slurpee)
In my last quick clip, I demonstrated how to take a bottle of soda and freeze it on command. I received many requests for a more detailed article on this, so here we go. This "super cool" trick works with cans of soda too, not just bottles!

Hack Like a Pro: How to Get Even with Your Annoying Neighbor by Bumping Them Off Their WiFi Network —Undetected
Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

How To: Beginner's Guide to OWASP Juice Shop, Your Practice Hacking Grounds for the 10 Most Common Web App Vulnerabilities
Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

How To: Crack Password-Protected Microsoft Office Files, Including Word Docs & Excel Spreadsheets
Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.

Warning: Sensitive Info You Black Out in Images Can Be Revealed with a Few Quick Edits on Your iPhone
These days, most images we post online or share with others come from our smartphones. Whenever personal data is in them, such as debit card numbers, addresses, phone numbers, passwords, and other sensitive information, it's easy to jump into your iPhone's markup tools to black out the text before sharing. But a digital marker may not hide everything.

How To: Use Burp & FoxyProxy to Easily Switch Between Proxy Settings
One of the best ways to dig into a website and look for vulnerabilities is by using a proxy. By routing traffic through a proxy like Burp Suite, you can discover hidden flaws quickly, but sometimes it's a pain to turn it on and off manually. Luckily, there is a browser add-on called FoxyProxy that automates this process with a single click of a button.

How To: Dial These Secret Codes to See if Someone Is Hijacking Calls & Texts on Your iPhone
Malevolent hackers can divert your incoming calls and texts to any number they want, and they don't need to be a criminal mastermind to do it. Even friends and family members can reroute your incoming calls and messages so that they know exactly who's trying to reach you, and all it takes is seconds of access to your iPhone or wireless account. These secret codes can help uncover them.

How To: Crack Shadow Hashes After Getting Root on a Linux System
After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

How To: 15 Hidden iMessage Features for iPhone You Probably Didn't Know About
There are many things Apple doesn't tell you about its products, and that's definitely the case when it comes to its Messages app. Hidden features lurk in your SMS and iMessage conversations just waiting to be found, and we've unearthed some of the most secret ones.

How To: Exploit EternalBlue on Windows Server with Metasploit
Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

How To: The Easiest Way to Secretly Record Someone's Conversation with Your iPhone
Your iPhone's built-in Voice Memos app is a great way to record the audio around you, whether it be conversations, lectures, meetings, interviews, discussions, chitchat, gossip, or other kinds of talks. But if your goal is to record audio on the down-low without being noticed, you'll need to know the hidden shortcut.
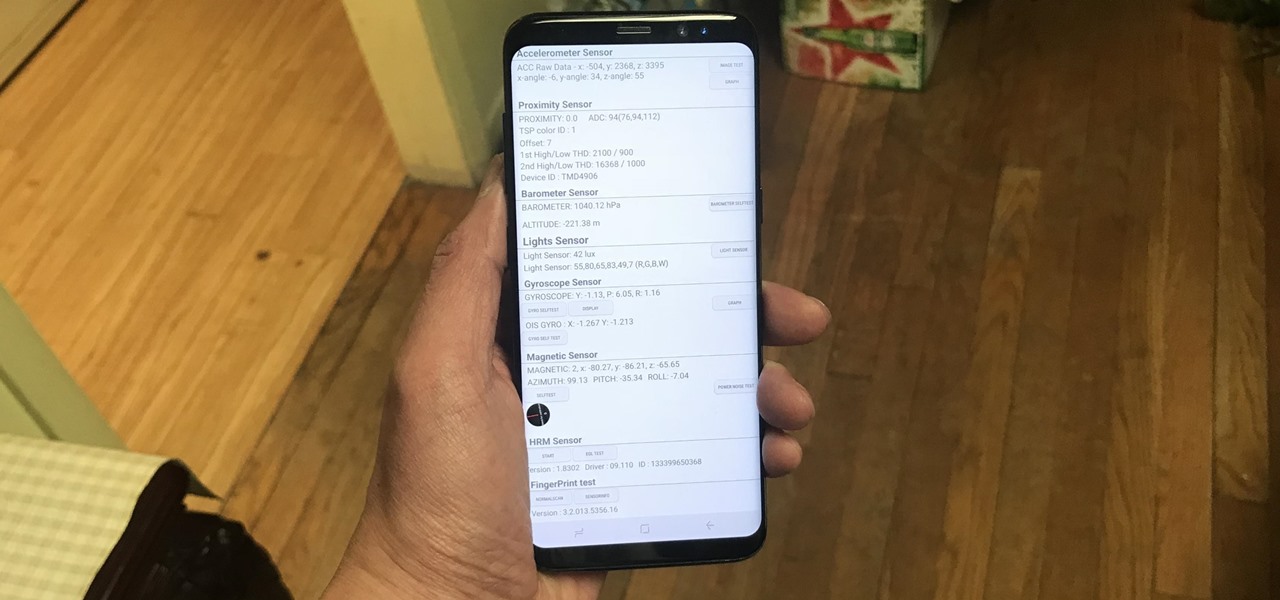
How To: Test Your Samsung Phone by Using Secret Code *#0*#
Besides obvious features like a touchscreen and biometric sensors, the modern smartphone comes with an array of state-of-the-art hardware in the form of various sensors that help your device sense the environment around it. And if you have a Samsung handset, chances are, you have a handy feature built in that enables you to check if these sensors are functioning 100 percent.

How To: Get Root with Metasploit's Local Exploit Suggester
So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.
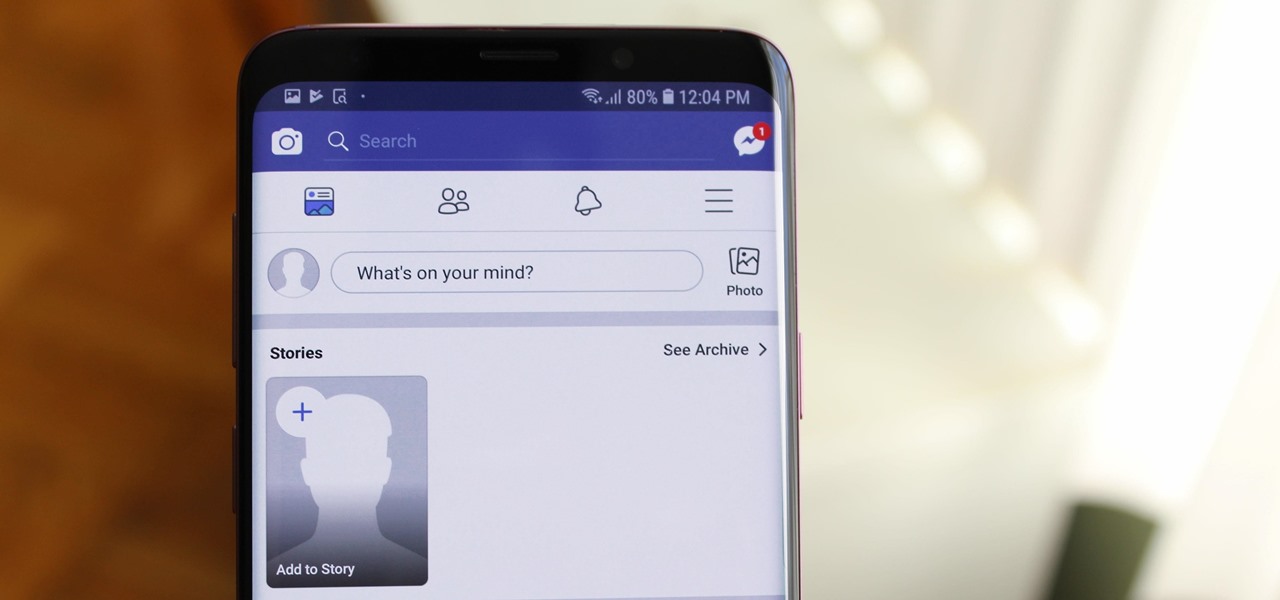
How To: Hide Stories in Your Facebook Feed on iPhone or Android
When Facebook introduced Stories in 2017, many users despised the Snapchat-like feature on their main page. However, despite the outcry, Facebook doesn't plan to let you remove it. But you don't have settle for this. With the help of some third-party apps, you no longer have to deal with Stories.

How To: The Best Settings to Use for Pro Mode in Your Galaxy S20's Camera App
No matter how many camera improvements a phone adds, you're always better off using manual mode. Known as "Pro Mode" on the Galaxy S20, this feature can remove Samsung's pre- and post-processing from photos, putting you in total control.
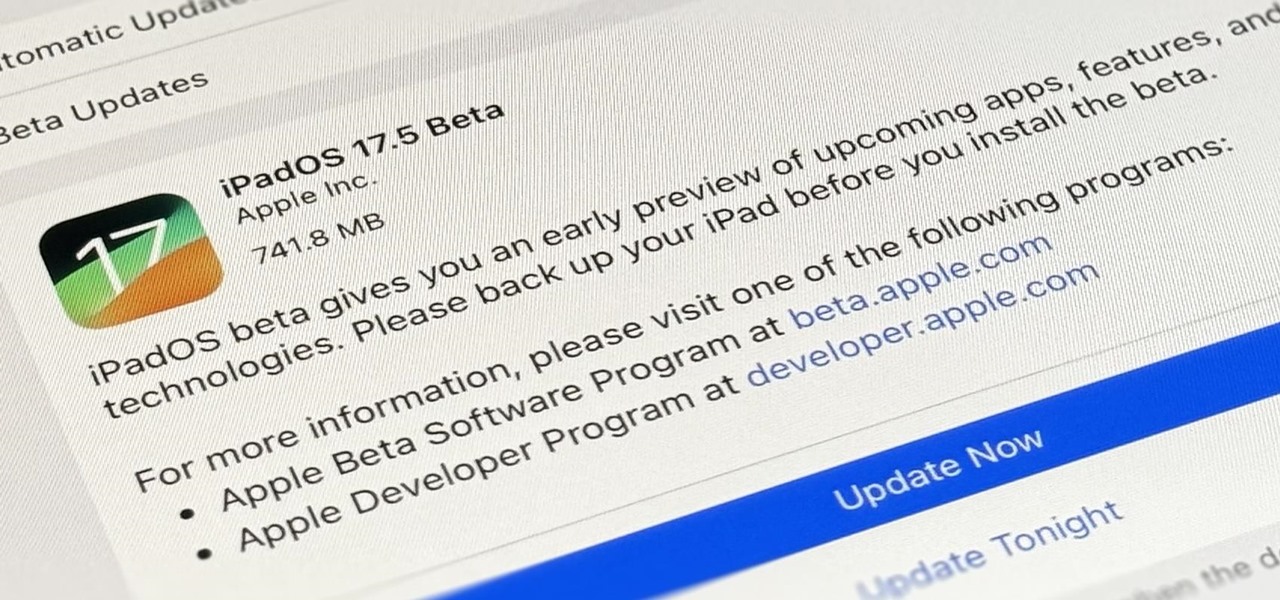
How To: Download and Install iPadOS 17.5 Beta on Your iPhone to Explore New Features Before Everyone Else
Apple's developer conference, where iPadOS 18 will be revealed, is just around the corner. But before we get there, there's still work to be done on iPadOS 17. That brings us to iPadOS 17.5 — and you can test drive it on your iPad right now before the masses.
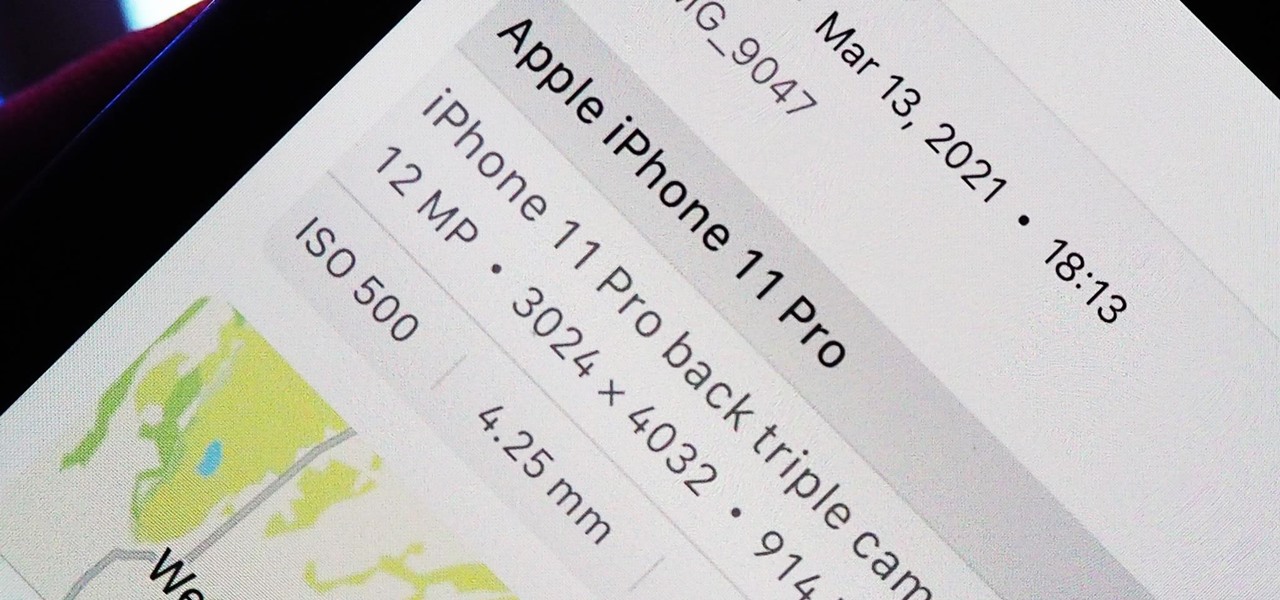
How To: Revert Spoofed Photos & Videos in iOS 15 to Their Original Locations & Dates
Apple introduces several new privacy settings with iOS 15, including the ability to better manage the metadata in your photos. With just a few taps, you can effectively spoof a photo's geolocation and change its creation date and time, providing a sort of disguise over your personal information. If you constantly take and share photos, it's a welcomed feature, but its results are not permanent and can be reversed.

How to Hack Wi-Fi: Capturing WPA Passwords by Targeting Users with a Fluxion Attack
With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

How To: The Top 80+ Websites Available in the Tor Network
There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

The Hacks of Mr. Robot: How to Hide Data in Audio Files
Welcome back, my hacker apprentices! A you know, Mr. Robot is my favorite TV show this year, and not just for the realistic hacking. Rami Malek, the actor who plays Elliot, is incomparable in his depiction of a young man with social anxiety who is alienated from a superficial, materialistic society and wants to make a better world. I believe we will see a lot more of this actor in coming years.

How To: Check Your Android Phone's DPI Value to See the Screen Density
There are at least 24,000 different Android devices, and they all have varying hardware components. This is why many developers publish several unique variants of their apps, which, among other things, helps accommodate all of the different display sizes and resolutions on Android phones and tablets.
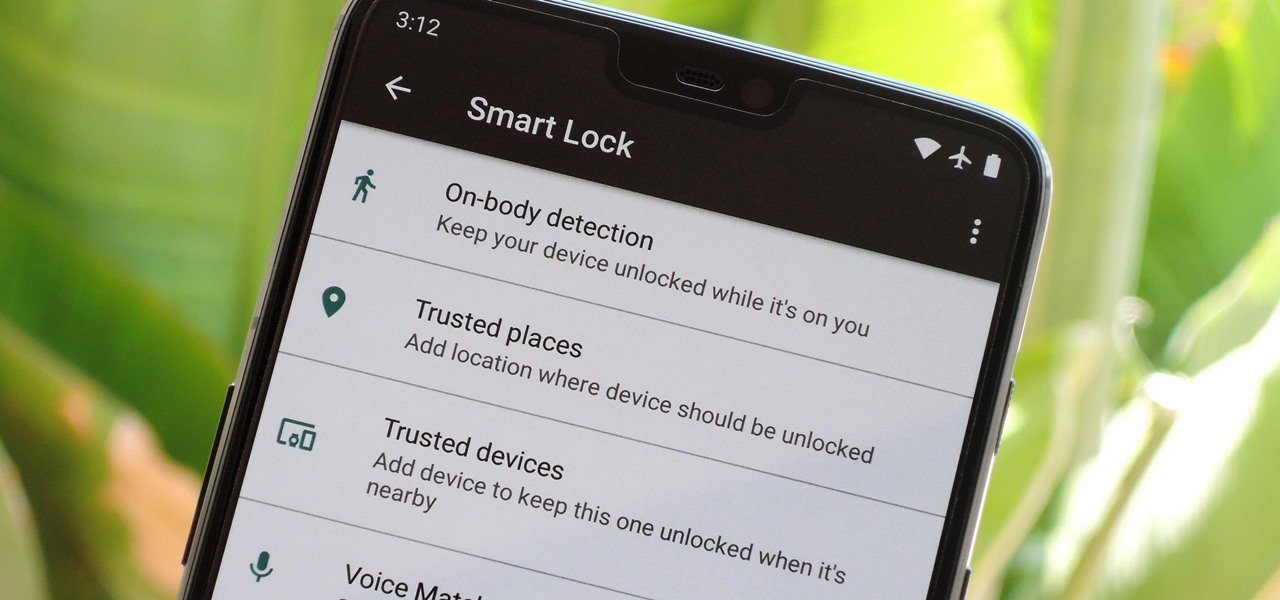
How To: 10 Troubleshooting Steps to Fix Smart Lock & Trusted Places on Any Android Device
When it works, Android's Smart Lock feature is incredible. There's no need to enter your PIN when your phone "knows" it's in your hands — just unlock and go. But Smart Lock, particularly its Trusted Places feature, can be finicky sometimes.
How To: Root the Pixel 5 & Still Pass SafetyNet — Full Guide for Beginners & Intermediate Users
The Pixel 5 is a great value proposition in this era of $1,500 phones. With its reasonable price tag, fully open-sourced software, and unlockable bootloader, it's also an ideal phone for rooting.

How To: Use the Buscador OSINT VM for Conducting Online Investigations
For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

How To: Pair a PlayStation 4 DualShock Controller to Your Chromecast with Google TV
While Google Stadia currently needs to be sideloaded on Chromecast with Google TV, there are a handful of games that are compatible with the streaming device and require a gamepad. But you don't need to buy a specific controller just for your Chromecast, you can use one you already have lying around.

How To: Secretly Take Photos on Android Without Launching Your Camera App
The art of taking secret photos is one that requires keen awareness and skill. Not only do you need to ensure that your subject remains oblivious, but you also need to make sure that no one near you notices what you're attempting to do. It's great when you buddy is acting a fool, but sucks when they stop their shenanigans when they notice you pulling out your camera phone in an effort to evade your picture.
How To: Root Your Pixel 3a with Magisk
The Pixel 3a came out of nowhere and flexed its muscles to show the industry that you can have a great phone without a hefty price tag. Since Pixel smartphones are first-party devices straight from Google, you can be sure you'll have root access one way or another. For right now the method used to get your Pixel 3a rooted will take a few steps, but they go by real quick.
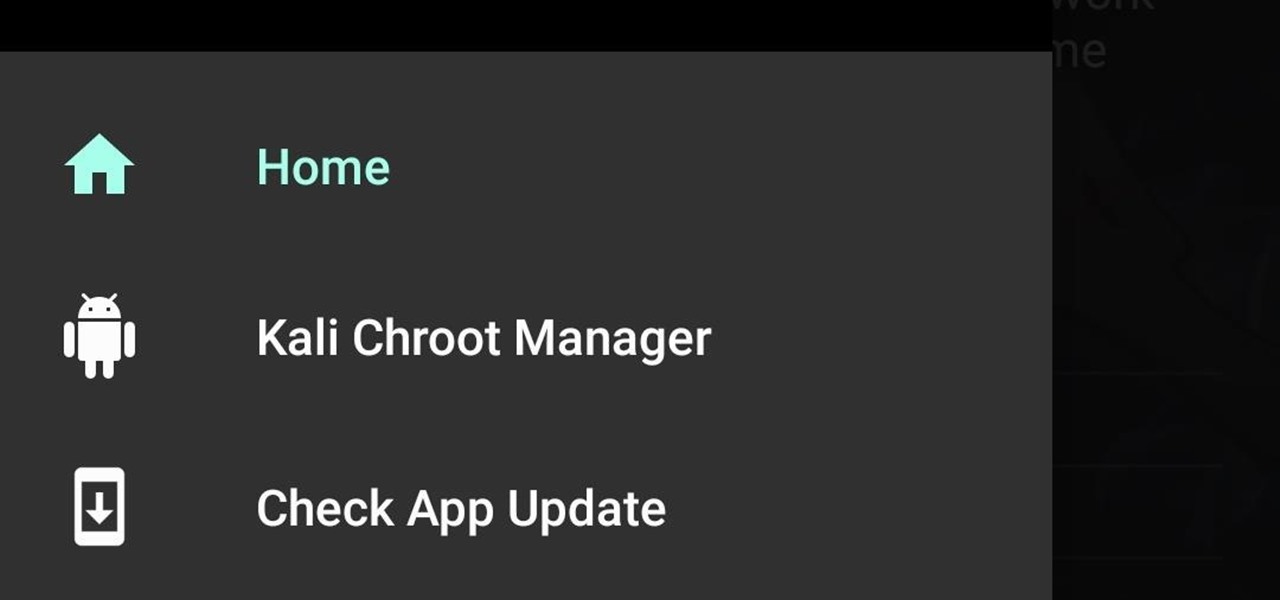
How To: Build and Install Kali Nethunter (The New Version) On a Supported Android Device Running Android 6.0.1
Hi guys. Hope you all had a good Christmas , today i have a tutorial for you.

Making Electromagnetic Weapons: EMP Generator, Part One
In this series, I'll be exploring electromagnetic weapons, how to build them, their function and application to the future, and the amazing possibilities electromagnetism has to offer. First, the electromagnetic pulse generator, or EMP. You've probably heard of these before, and their devastating effects on electronics. A simple EMP consists of a capacitor, transformer, trigger, and coil of copper wire. This, when triggered, would produce an intense magnetic field for a brief period, similar ...
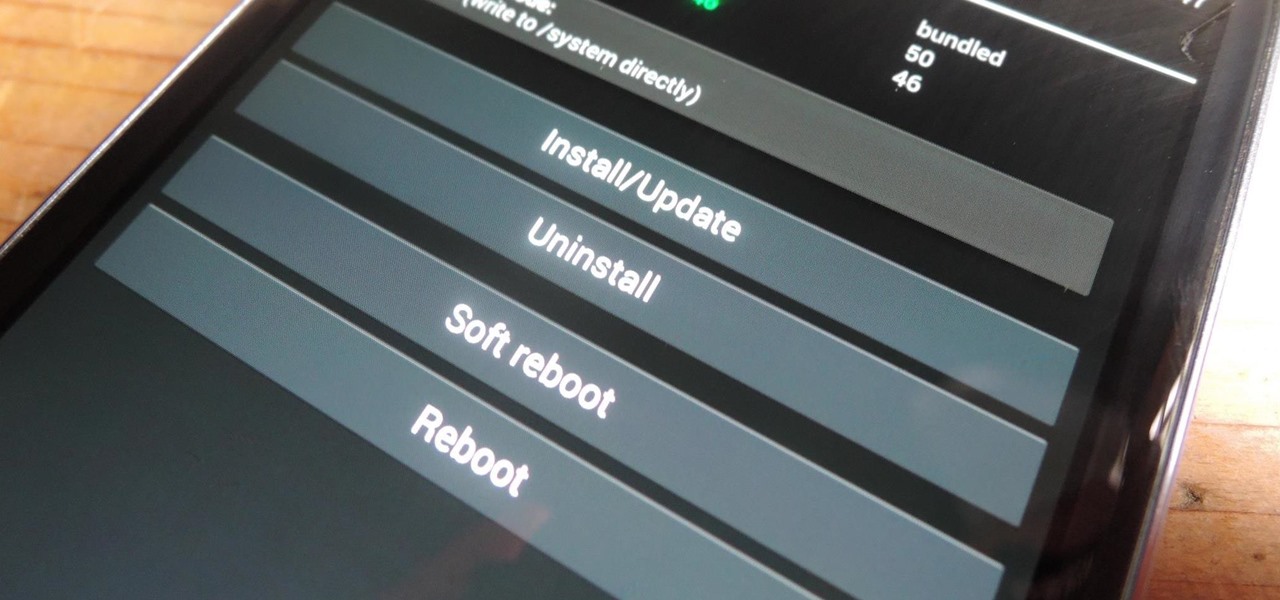
How To: Activate Modules After Installation in Xposed Installer
Created by by XDA developer rovo89, the Xposed Framework allows you to quickly search for, download, and install new modules that allow various forms of customization for your Android device.

How To: Make Spoofed Calls Using Any Phone Number You Want Right from Your Smartphone
Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to fool you into picking up. Turns out, making a spoofed call is something anybody can do — even you.






